In today’s hyper-connected world, your phone number is more than just a way to receive calls—it's a key to your digital identity. From two-factor authentication (2FA) to syncing contacts and restoring data, your number ties together multiple accounts and devices. However, sharing it carelessly can expose you to spam, phishing, and even account takeovers. The challenge lies in using your number where necessary while minimizing exposure and risk.
This guide walks through the secure process of adding your phone number across platforms and devices, ensuring both functionality and protection. Whether you're setting up a new smartphone, linking social media profiles, or enabling 2FA, these steps help maintain control over your personal information.
Why Security Matters When Sharing Your Phone Number
Your phone number is a persistent identifier. Unlike passwords, which can be changed, your number often stays with you for years—making it a prime target for malicious actors. Once compromised, attackers can use it to intercept verification codes, impersonate you, or gain access to accounts via SIM-swapping attacks.
According to the Federal Trade Commission (FTC), impersonation scams involving phone numbers increased by 70% between 2020 and 2023. This rise underscores the importance of being selective about where and how your number is used.
“Your phone number is not just contact info—it’s an authentication token. Treat it like a password.” — Dr. Linnea Ehri, Cybersecurity Researcher at Stanford University
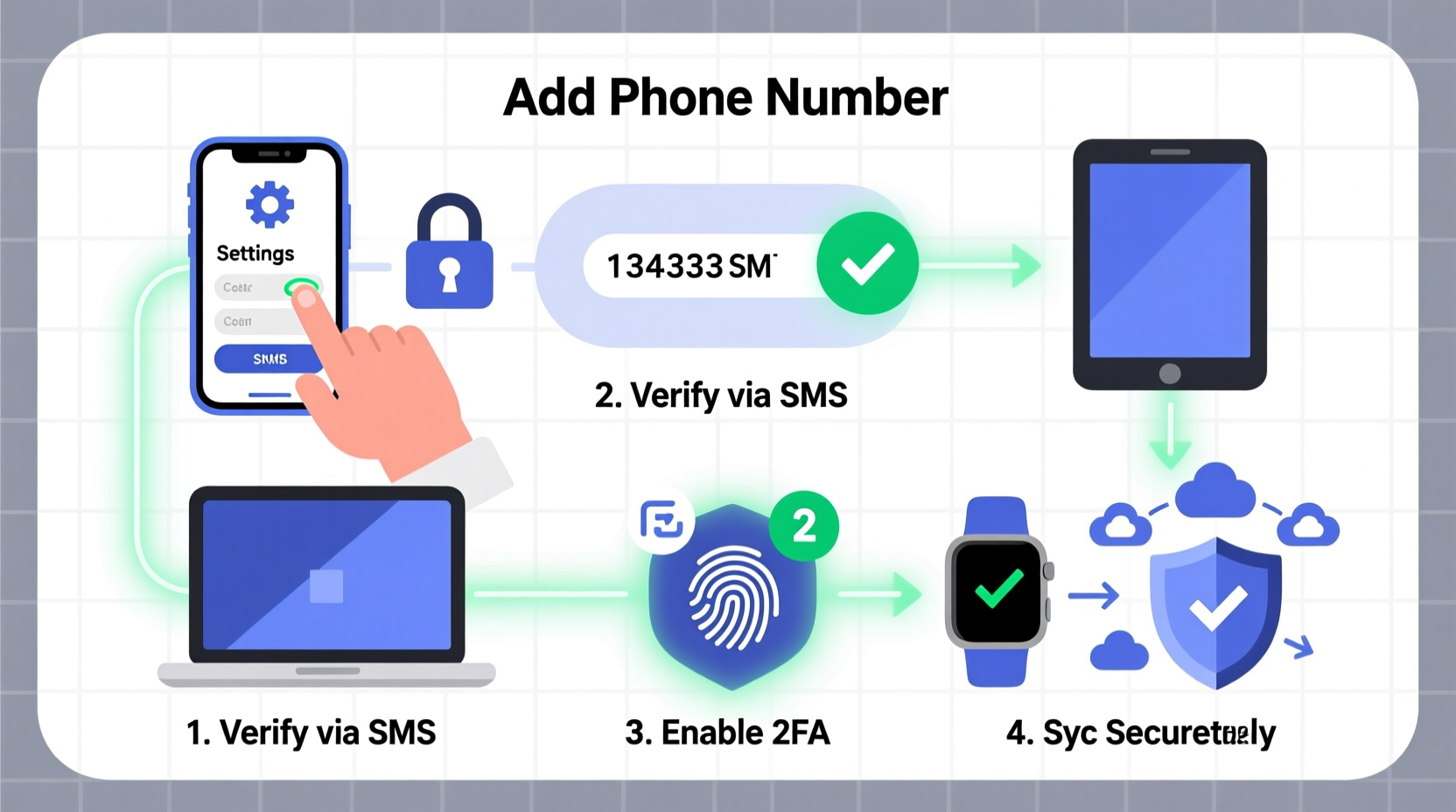
Step-by-Step: How to Add Your Phone Number Securely
Step 1: Audit Where Your Number Is Already Listed
Before adding your number anywhere new, review where it’s currently registered. Make a list of all active accounts—email, banking, social media, cloud storage, messaging apps—and note whether each one uses your number for login, recovery, or notifications.
Remove outdated entries. Many people keep old accounts active without realizing they still have their number attached. Log in or use account recovery tools to update or delete obsolete registrations.
Step 2: Enable Two-Factor Authentication Using App-Based or Hardware Methods First
If a service offers two-factor authentication (2FA), avoid using SMS-based verification if alternatives exist. SMS is vulnerable to interception through SIM swapping or SS7 protocol exploits.
Instead, opt for authenticator apps (like Google Authenticator, Authy, or Microsoft Authenticator) or hardware keys (such as YubiKey). These generate time-based codes locally on your device, reducing reliance on your phone number.
Only use SMS 2FA when no other option is available—and consider using a secondary number (see Step 5) in such cases.
Step 3: Set Up Device Syncing with Controlled Permissions
When setting up a new smartphone, tablet, or computer, syncing your contacts and settings often requires entering your phone number. To do this securely:
- Use end-to-end encrypted sync services (e.g., Apple iCloud with Advanced Data Protection, or ProtonMail’s encrypted contact sync).
- Review permissions during setup. Disable unnecessary data sharing, especially with third-party apps.
- Verify that backups are encrypted and stored under your control.
On Android, ensure “Find My Device” is enabled but restrict ad personalization and location sharing. On iOS, enable Lockdown Mode for high-risk users who may be targeted.
Step 4: Use Primary Number Only for Trusted Services
Reserve your primary mobile number for essential, high-trust accounts: your bank, main email provider, and cellular carrier. Avoid giving it to retail stores, food delivery apps, or online forums.
For less critical sign-ups, use alternative methods:
- Email-based registration
- Disposable or virtual numbers (e.g., Google Voice, TextNow)
- Anonymous login options (Apple Sign In, Login.gov)
Step 5: Consider a Secondary Number for Public or Semi-Public Use
A virtual phone number acts as a buffer between your real identity and the outside world. Services like Google Voice, MySudo, or Burner allow you to create a separate number linked to your main line—but only you control forwarding and access.
Use this secondary number for:
- Signing up for newsletters or e-commerce sites
- Online marketplaces (e.g., Craigslist, Facebook Marketplace)
- Temporary verifications (ride-sharing, short-term rentals)
You can disable or change the virtual number anytime, preserving your primary number’s integrity.
Do’s and Don’ts: Managing Phone Number Exposure
| Do’s | Don’ts |
|---|---|
| Use app-based 2FA instead of SMS when possible | Share your number on public forums or social media bios |
| Set up call and message filtering on your device | Click links in unsolicited texts claiming to be from your carrier |
| Enable carrier-level anti-spam protection (e.g., T-Mobile Scam Shield, Verizon Call Filter) | Give your number to unknown callers or automated surveys |
| Regularly check which accounts have your number listed | Use your real number for throwaway accounts |
Mini Case Study: Recovering from a SIM Swap Attack
Sarah, a freelance designer, lost access to her email and cryptocurrency exchange accounts within minutes. She received a notification that her number had been ported to a new carrier—without her consent. An attacker had used social engineering to convince her mobile provider to transfer her number to a different SIM card.
With SMS-based 2FA enabled, the attacker reset passwords and drained her accounts. It took Sarah over two weeks to regain control, involving ID verification, legal documentation, and contacting support teams across platforms.
Afterward, she implemented several changes:
- Migrated all 2FA to authenticator apps
- Set up a PIN with her carrier to prevent unauthorized transfers
- Started using a Google Voice number for non-critical accounts
Her experience highlights how easily a phone number can become a weak link—even for tech-savvy individuals.
Essential Checklist for Secure Number Management
- ✅ Audit all accounts currently using your phone number
- ✅ Replace SMS-based 2FA with app-based or hardware alternatives
- ✅ Set a port validation PIN with your mobile carrier
- ✅ Enable built-in spam protection on your phone
- ✅ Create a secondary virtual number for low-trust services
- ✅ Regularly review privacy settings on social media and cloud accounts
- ✅ Never share your number publicly (e.g., in bios, comment sections)
Frequently Asked Questions
Can I remove my phone number from an account entirely?
Yes, in many cases. Some platforms allow replacing your number with an email address or backup code for recovery. Check the security or account settings section. If removal isn’t possible, consider using a virtual number as a compromise.
Is it safe to use Google Voice for 2FA?
It depends. While Google Voice adds a layer of separation, it’s still tied to your Google account. If that account is compromised, so is your Voice number. For higher security, prefer authenticator apps or hardware tokens. Use Google Voice only when SMS is the only alternative.
How do I prevent someone from hijacking my number?
Contact your carrier to set up a port-out PIN or account passcode. This prevents unauthorized transfers. Also, limit public exposure of your number and avoid reusing it across disposable accounts. Monitor for unexpected service disruptions, which could indicate a porting attempt.
Conclusion: Take Control of Your Digital Identity
Your phone number is a powerful piece of personal data—one that shouldn’t be handed out casually. By following a structured approach to its use, you protect not just your privacy but also the integrity of your online accounts.
Start today: clean up outdated registrations, switch to stronger 2FA methods, and establish boundaries for where your number goes. Small changes now can prevent major breaches later. Your digital safety isn’t just about passwords—it’s about every piece of information you share, including the number in your pocket.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?