In an age where smartphones hold personal messages, financial data, photos, and location history, privacy is paramount. Yet there are legitimate reasons someone might need temporary access to another person’s device — from helping a family member troubleshoot a technical issue to monitoring a child’s digital safety. The key distinction lies in consent. Accessing a phone without permission is a breach of trust and often illegal. But when done transparently and with explicit approval, it can be both ethical and beneficial.
This guide outlines how to responsibly access someone’s phone only when authorized, emphasizing communication, boundaries, and respect for digital autonomy.
Why Permission Matters: Legal and Ethical Foundations
Digital privacy is increasingly recognized as a fundamental right. In many jurisdictions, unauthorized access to another person’s phone — even by a spouse or parent — can violate laws such as the U.S. Computer Fraud and Abuse Act or the UK’s Investigatory Powers Act. Even if no harm is intended, bypassing passcodes or using spyware without consent may lead to legal consequences.
Consent transforms the act from intrusion into collaboration. When someone willingly shares their passcode or grants screen time permissions, they retain control over what is accessed and for how long. This mutual understanding builds trust rather than eroding it.
“Digital consent isn’t just about legality — it’s about respect. Just because you *can* unlock someone’s phone doesn’t mean you *should*, unless they’ve clearly said yes.” — Dr. Lena Torres, Digital Ethics Researcher at the Center for Responsible Technology
Common Scenarios Where Access May Be Appropriate
Not all requests to view a phone are equal. Context determines whether access is justified. Below are real-world situations where permission-based access makes sense:
- Troubleshooting technical issues: A partner asks for help fixing a malfunctioning app or setting up email.
- Parental oversight: A parent reviews a teenager’s messaging activity after discussing online risks and agreeing on usage rules.
- Caregiving responsibilities: An adult child accesses an elderly parent’s phone to manage medical appointments or medication reminders.
- Emergency preparedness: Couples exchange passcodes in case one is incapacitated during a crisis.
- Device repair assistance: A friend helps reset settings before selling a phone, with full transparency.
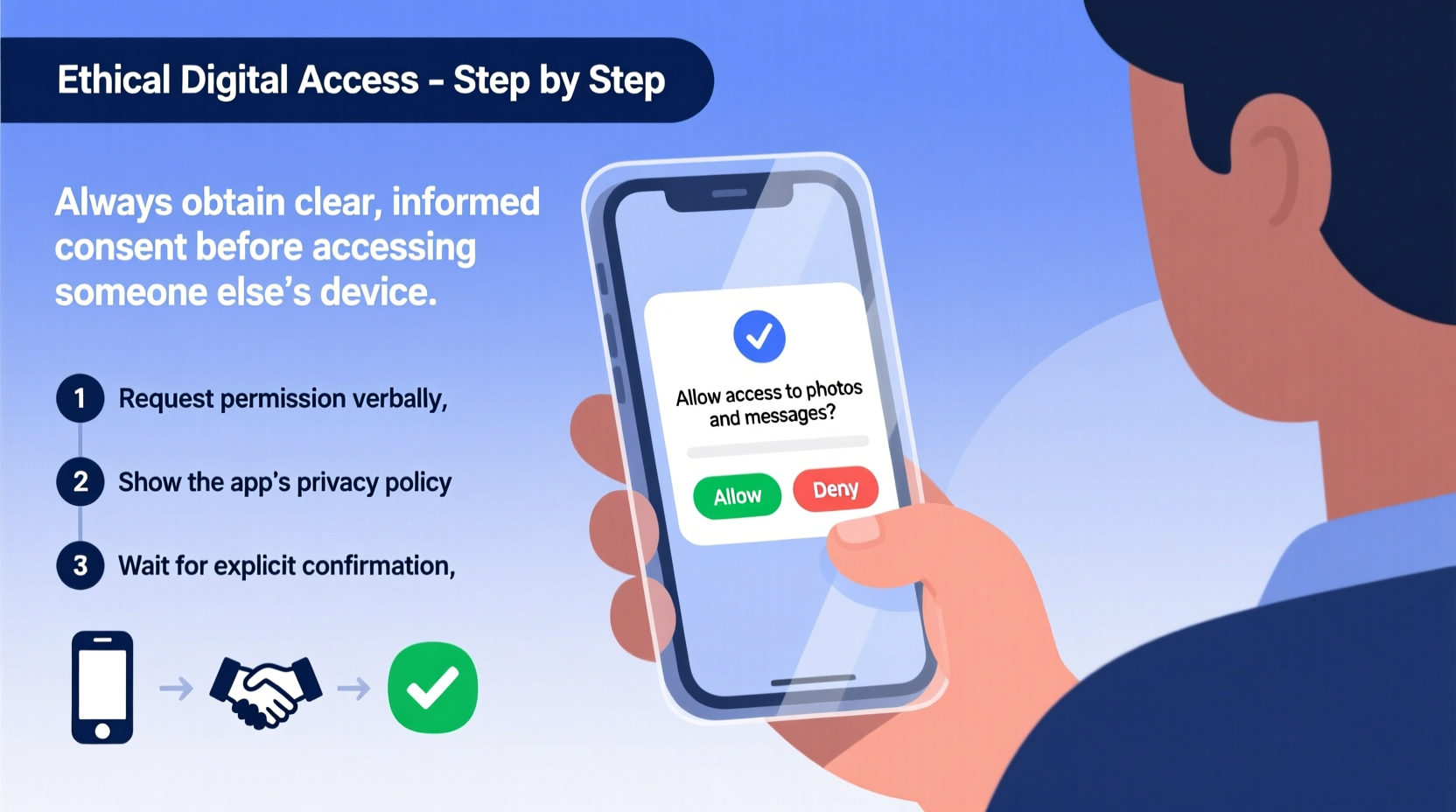
Step-by-Step Guide to Ethically Access a Phone With Consent
Even with permission, the process should be structured to prevent misunderstandings. Follow these steps to ensure respectful and purposeful access:
- Initiate an open conversation: Explain why you need access, what you plan to do, and how long it will take. For example: “I want to help set up your new banking app. Can I borrow your phone for five minutes?”
- Obtain clear verbal or written consent: Ensure the person understands and agrees. If the user is a minor or has cognitive limitations, involve a guardian or caregiver.
- Use only the agreed-upon method: If given a passcode, use it only once for the stated purpose. Do not save biometrics (like fingerprints) or write down passwords.
- Stay within defined boundaries: Avoid checking unrelated apps, messages, or files outside the scope of the request.
- Log out and lock immediately: After completing the task, close all opened apps, log out of any accounts accessed, and re-lock the device.
- Debrief afterward: Confirm the task was completed and ask if they have concerns. Reinforce that their privacy remains a priority.
Do’s and Don’ts of Permission-Based Phone Access
| Do’s | Don’ts |
|---|---|
| Ask before touching the device | Assume access is okay because you’re in a relationship |
| Explain exactly what you’ll do | Scroll through old messages “just to check” |
| Respect revocation of consent at any time | Install tracking software without ongoing discussion |
| Use screen sharing instead of physical access when possible | Take screenshots or save private information |
| Delete browsing history after troubleshooting | Leave the phone unlocked or unattended |
Real Example: Supporting a Parent with Technology
Mark, a 34-year-old IT consultant, noticed his 72-year-old father struggling to use video calling apps to connect with grandchildren. After several frustrating attempts, Mark asked, “Can I show you how to use FaceTime? I’ll need to unlock your phone and set it up — is that okay?” His father agreed, and Mark walked him through the process step by step, keeping the session focused and educational.
He didn’t open other apps, avoided personal emails, and ended the session by asking, “Would you like me to write down the steps for next time?” This approach preserved dignity, encouraged independence, and strengthened their relationship — all while maintaining ethical boundaries.
Tools That Support Transparent Access
Modern operating systems offer built-in features designed for safe, consensual access:
- Apple Screen Sharing (iOS): Allows remote viewing of a user’s screen during a FaceTime call, useful for guiding someone through a process without direct access.
- Google’s Family Link: Enables parents to monitor app usage, set screen time limits, and approve downloads — but only when linked with a child’s Google account and accompanied by open dialogue.
- Accessibility Features: VoiceOver or Switch Control can be temporarily enabled to assist users with disabilities, provided they understand and accept the changes.
These tools work best when introduced collaboratively, not imposed silently.
Frequently Asked Questions
Can I legally access my child’s phone?
Yes, if they are under 18 and you are the legal guardian. However, legality doesn’t replace ethics. Open conversations about digital safety and agreed-upon monitoring practices foster better long-term outcomes than secret surveillance.
What if someone gives me permission but later regrets it?
Respect their change of heart immediately. Revoke any saved credentials, delete any stored data, and reaffirm their right to digital privacy. Trust can be rebuilt through accountability.
Is it ever okay to access a partner’s phone without asking?
No. Even in committed relationships, phones contain private thoughts and communications. Surprise checks damage trust and can escalate into conflict. If concerns exist about safety or infidelity, seek counseling instead of resorting to covert access.
Checklist: Ensuring Ethical Access Every Time
- ✅ Have a clear, legitimate reason for needing access
- ✅ Discuss the purpose openly and obtain verbal or written consent
- ✅ Limit access to only what’s necessary
- ✅ Avoid saving passwords, taking screenshots, or copying data
- ✅ Lock the device and confirm completion of the task
- ✅ Be prepared to stop if consent is withdrawn
Conclusion: Respect Is the Foundation of Digital Trust
Technology evolves rapidly, but human values remain constant. The ability to access someone’s phone comes with significant responsibility. When permission is freely given, respected, and time-bound, it becomes a tool for support — not surveillance. Whether helping a loved one navigate a new app or ensuring a child’s safety online, the most effective approach is always rooted in honesty, empathy, and mutual agreement.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?