Incognito mode in Google Chrome offers privacy by not saving browsing history, cookies, or form data. While useful for personal users, it poses a significant challenge for organizations, educational institutions, and parents who need to monitor or manage online activity. Unrestricted use of incognito mode can undermine content filtering, security policies, and digital accountability. Fortunately, several effective methods exist to disable or restrict this feature—depending on your environment and technical capabilities.
This guide provides actionable strategies to block incognito mode across different settings, from enterprise networks to home computers, ensuring greater oversight and safer browsing environments.
Understanding the Risks of Uncontrolled Incognito Mode
While incognito mode doesn’t make users anonymous online—it only prevents local data storage—its misuse can bypass monitoring tools and content filters. In schools, students may use it to access restricted websites. In workplaces, employees might evade productivity tracking. At home, children could view inappropriate content without leaving a trace on the device.
The key issue is that incognito mode disables critical logging mechanisms, making it harder to enforce acceptable use policies. For administrators responsible for digital safety and compliance, allowing unrestricted access to incognito mode defeats the purpose of deploying monitoring software or web filters.
“Disabling incognito mode is a foundational step in any managed browsing strategy. It closes a major loophole in digital supervision.” — Dr. Alan Reed, Cybersecurity Consultant for K–12 Education
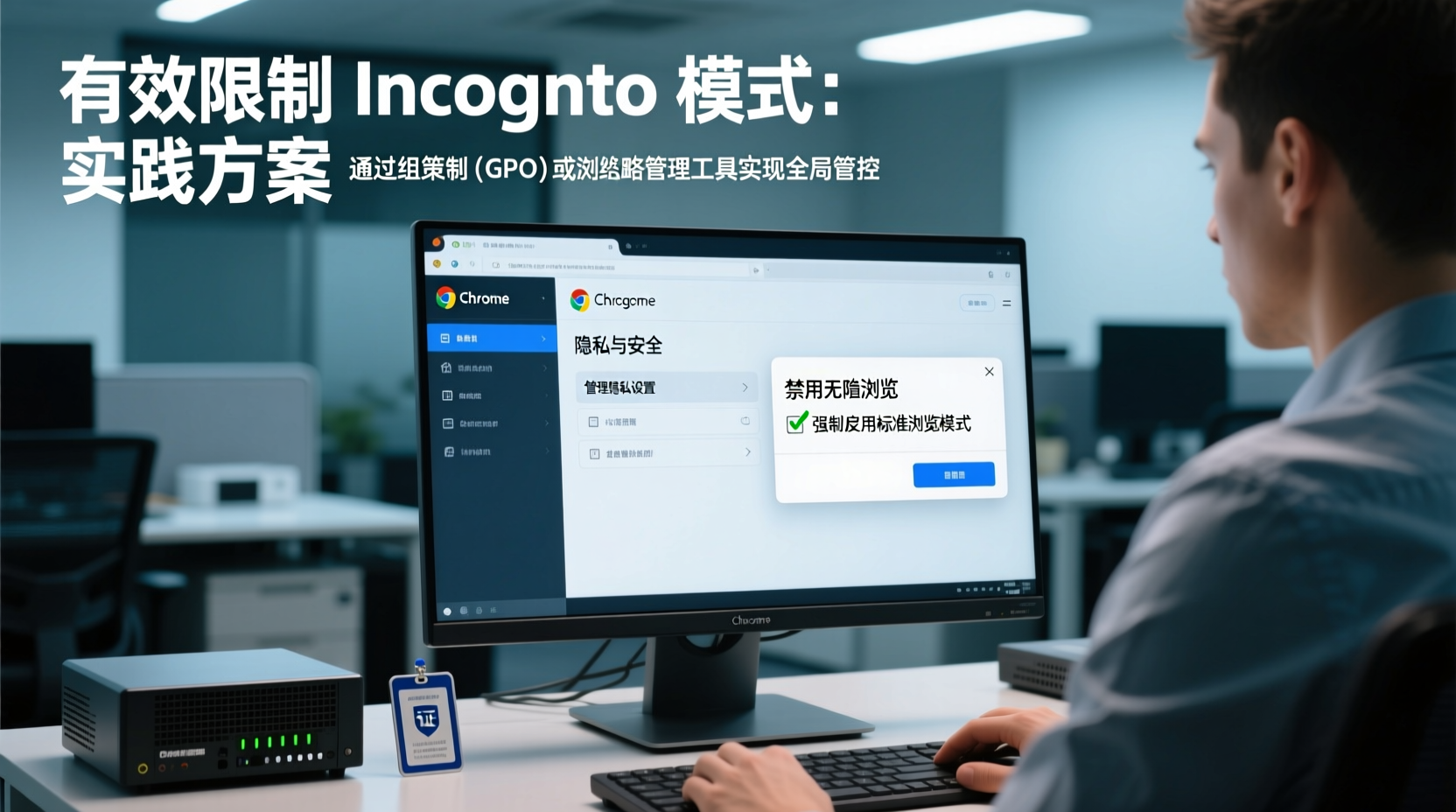
Step-by-Step: Restricting Incognito Mode via Group Policy (Windows)
For organizations using Windows and Chrome Browser in a domain environment, Group Policy is the most reliable method to disable incognito mode across multiple devices.
- Download the Chrome ADM/ADMX templates from the official Google Admin website and install them into your Group Policy Central Store.
- Open the Group Policy Management Console (GPMC) and create or edit an existing GPO linked to the target Organizational Unit (OU).
- Navigate to User Configuration > Policies > Administrative Templates > Google > Google Chrome.
- Locate the setting: “Allow Incongnito mode” and set it to “Disabled”.
- Enable the policy: “Incognito mode availability” and set it to “Disabled” to fully block access.
- Apply and force a group policy update on client machines using
gpupdate /force.
Once applied, users will see a message stating that incognito mode has been disabled by the administrator when attempting to open a private window.
Using Chrome Browser Cloud Management (CBCM) for Remote Control
For environments without Active Directory—such as cloud-based schools or remote teams—Chrome Browser Cloud Management offers a scalable alternative.
CBCM allows IT admins to enforce browser policies directly through the Google Admin console, regardless of device location. This is especially useful for BYOD (Bring Your Own Device) programs or hybrid work setups.
Steps to Disable Incognito Mode via CBCM:
- Sign in to the Google Admin Console.
- Navigate to Devices > Chrome > Settings > Users & Browsers.
- Select the organizational unit you want to apply the policy to.
- Search for “Incognito mode availability” under User settings.
- Set the value to “Disabled”.
- Click “Save” and allow up to 24 hours for policies to sync.
Note: Devices must be enrolled in CBCM and running Chrome 75 or later. Users do not need to be signed in for policies to apply if device-level enforcement is configured.
Blocking Incognito Mode on macOS and Linux Systems
Administrators managing non-Windows systems can still enforce restrictions using platform-specific configuration files.
On macOS:
Create a property list (.plist) file at /Library/Preferences/com.google.Chrome.plist with the following entry:
<key>IncognitoModeAvailability</key> <integer>1</integer>
Where 1 disables incognito mode entirely. Use MDM (Mobile Device Management) solutions like Jamf or Mosyle to deploy this setting across managed Macs.
On Linux:
Edit or create the JSON policy file at /etc/opt/chrome/policies/managed/incognito_policy.json:
{
\"IncognitoModeAvailability\": 1
}
This method works on Debian, Ubuntu, and other Chrome-supported Linux distributions.
Parental Controls: Managing Incognito Mode at Home
Families seeking to protect children from unmonitored browsing have fewer native options but can leverage third-party tools and supervised accounts.
Google Family Link allows parents to manage their child’s Chrome experience on Android and iOS, though direct incognito blocking requires additional steps:
- Use a dedicated parental control app like K9 Web Protection or Net Nanny, which override browser settings and block private browsing attempts.
- Set up a standard user account (not administrator) on the family computer and apply local group policies or registry edits to disable incognito.
- Enable DNS-level filtering through services like OpenDNS or Cloudflare for Families, which log all requests—even from incognito sessions.
Comparison of Methods: Which Solution Fits Your Needs?
| Method | Best For | Remote Enforcement | Requires Admin Rights | Effectiveness |
|---|---|---|---|---|
| Group Policy (Windows) | Enterprises, schools with AD | No (local network) | Yes | ★★★★★ |
| Chrome Browser Cloud Management | Distributed teams, cloud-first orgs | Yes | Yes | ★★★★☆ |
| MDM (macOS/Linux) | Apple or Linux environments | Yes (via MDM) | Yes | ★★★★☆ |
| Local Policy Files | Small offices, single devices | No | Yes | ★★★☆☆ |
| Parental Control Apps | Home users, families | Limited | Yes (initial setup) | ★★★☆☆ |
Mini Case Study: A School District Closes the Privacy Loophole
The Lincoln County School District in Oregon noticed a spike in policy violations despite having web filters in place. Investigation revealed that students were launching incognito windows to bypass content restrictions during lab hours.
The IT team responded by deploying Chrome policies via Group Policy Objects across all student workstations. They disabled incognito mode and integrated DNS filtering with Cisco Umbrella for real-time monitoring. Within two weeks, blocked category incidents dropped by 68%, and teachers reported improved focus during computer-based lessons.
“We weren’t just blocking a feature—we were reinforcing our digital citizenship curriculum with consistent enforcement,” said Maria Tran, the district’s IT director.
Checklist: How to Secure Chrome Against Unauthorized Incognito Use
- ✅ Identify your environment: Windows, macOS, Linux, or mixed?
- ✅ Determine administrative access level (local or domain-wide).
- ✅ Choose the appropriate method: Group Policy, CBCM, MDM, or third-party tool.
- ✅ Test the configuration on one device before full deployment.
- ✅ Monitor logs to confirm incognito attempts are blocked.
- ✅ Communicate changes to users to prevent confusion or workarounds.
- ✅ Review policies quarterly to ensure ongoing compliance.
FAQ
Can users bypass these restrictions with third-party browsers?
Yes. If users install alternative browsers like Firefox or Edge, they may still access private browsing. To prevent this, combine Chrome restrictions with application control policies that limit software installation.
Does disabling incognito mode affect regular browsing performance?
No. Disabling incognito mode only removes access to private sessions. Normal browsing functions remain unchanged, and page load times, extensions, and security features operate as usual.
Is it possible to allow incognito mode for some users but not others?
Yes. Using organizational units (OUs) in Active Directory or Chrome management console, you can apply policies selectively. For example, allow incognito for IT staff while blocking it for students or general employees.
Final Thoughts: Control Starts with Configuration
Restricting incognito mode in Chrome is not about eliminating privacy—it’s about maintaining accountability in environments where oversight matters. Whether you’re managing a classroom, corporate network, or family device, the tools exist to close this gap effectively.
Start with assessing your infrastructure, choose the right method for your needs, and implement controls consistently. Technology alone isn’t enough—combine it with clear policies and user education for lasting impact.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?