In today’s hyper-connected world, concerns about digital safety—especially for children, aging parents, or employees—are more relevant than ever. While the idea of monitoring a device through its IP address may sound like something from a spy thriller, the reality is far more nuanced. It's important to emphasize that any form of digital monitoring must be conducted within legal boundaries and with full transparency. This guide explores what is technically possible, what is legally permissible, and how to approach device monitoring responsibly.
Contrary to popular belief, an IP address alone does not provide direct access to a smartphone’s data, messages, or location in real time. However, when combined with proper tools and authorization, it can play a supportive role in broader monitoring strategies that prioritize privacy and consent.
Understanding IP Addresses and Mobile Devices
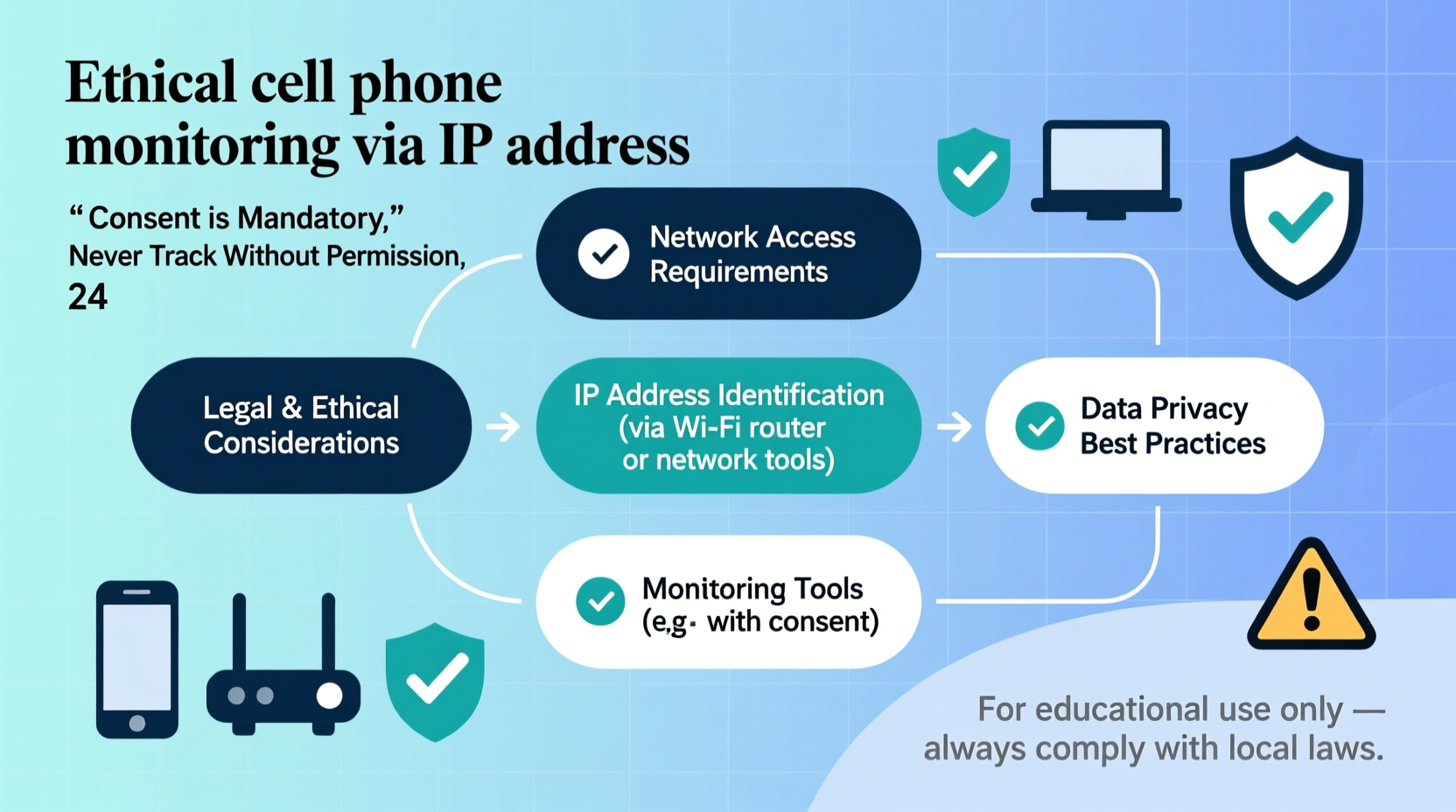
An IP (Internet Protocol) address is a unique identifier assigned to any device connected to a network. For mobile phones, this address changes frequently because smartphones typically connect via cellular networks or public Wi-Fi, both of which assign dynamic IPs. Unlike a home desktop on a fixed broadband connection, a mobile phone rarely holds the same IP for long.
There are two types of IP addresses: public and private. The public IP is visible to websites and services online, while the private IP is used internally by your router. When someone accesses the internet from a phone, servers see the public IP—but this only reveals general geographic location (often at the city or ISP level), not precise GPS coordinates.
Because mobile IPs change so often, tracking a device solely through its IP is impractical for continuous monitoring. Moreover, without lawful authority or user consent, attempting to trace or log another person’s IP activity may violate privacy laws such as the Electronic Communications Privacy Act (ECPA) in the U.S. or GDPR in Europe.
When Monitoring Is Ethical and Legal
Ethical monitoring hinges on three principles: consent, purpose, and proportionality. You may legally monitor a device if:
- You are a parent monitoring a minor child’s device for safety.
- You are an employer overseeing company-issued phones used during work hours.
- The owner of the device has explicitly granted permission.
In these cases, monitoring isn’t about invasion—it’s about protection. For example, parents might want to ensure their teenager isn’t engaging with harmful content online. Employers may need to safeguard sensitive corporate data. In all instances, openness is key. Secret surveillance erodes trust and risks legal consequences.
“Transparency is non-negotiable in digital monitoring. If you’re doing it right, there’s nothing to hide.” — Dr. Lena Patel, Cyberethics Researcher, Stanford University
Practical Steps for Responsible Device Oversight
If you have a legitimate reason to monitor a device, follow this ethical framework:
- Obtain explicit consent from the device user, unless they are a minor under your care.
- Use dedicated monitoring software designed for parental control or employee management.
- Leverage IP logs as one of many tools—not the primary method—for understanding network behavior.
- Respect privacy boundaries—avoid accessing personal messages or social media without justification.
- Review data periodically rather than conducting constant surveillance.
Some tools, like Google Family Link or Apple Screen Time, allow caregivers to view usage patterns, set screen limits, and receive alerts—all without needing to extract IP addresses manually. These platforms operate within secure ecosystems and comply with data protection standards.
How IP Data Can Support Monitoring (Without Overreach)
While you can’t “track” a phone live via IP, reviewing historical IP logs from router settings or monitoring apps can help answer questions like:
- Was the device connected to an unfamiliar network late at night?
- Is it frequently connecting to high-risk regions or suspicious domains?
- Has there been unauthorized access to a shared family account?
To retrieve IP history:
- Access your home router’s admin panel (usually via 192.168.1.1).
- Navigate to the \"Connected Devices\" or \"Logs\" section.
- Identify the phone by MAC address or device name.
- Note timestamps and associated public IPs (if logged).
- Cross-reference with external IP lookup tools like
iplocation.netfor approximate location.
This process doesn’t require hacking or third-party exploits—it uses standard networking features available to any network administrator.
Common Misconceptions and Risks
Many online forums promote misleading ideas about IP tracking, suggesting that anyone can pinpoint a phone’s exact location using just an IP. This is false. Real-time GPS tracking requires access to device-level services like Find My iPhone or Android Device Manager—none of which rely on IP alone.
| Misconception | Reality |
|---|---|
| You can track someone’s phone location using only their IP. | IPs give rough location (city/region), not street-level precision. |
| Monitoring without consent is acceptable if done for safety. | No—lack of consent may constitute illegal wiretapping or stalking. |
| All monitoring apps are safe and legal. | Some violate app store policies or collect excessive data. |
Mini Case Study: A Parent’s Responsible Approach
Sarah, a single mother of a 14-year-old, noticed her daughter becoming withdrawn and spending late nights on her phone. Concerned about cyberbullying or inappropriate contact, she initiated an open conversation. Together, they agreed to use Apple’s Screen Time to track usage and enable location sharing.
Sarah accessed weekly reports showing when the phone was used and which apps consumed the most time. She also reviewed Wi-Fi connection logs from their home router and noticed the phone briefly joined a neighbor’s unsecured network late one evening—likely due to automatic switching. Instead of reacting harshly, she discussed digital habits and agreed on new rules.
No secret tracking was involved. Trust was preserved. Safety improved.
Checklist: Ethical Monitoring Best Practices
- ☑️ Have a clear, justified reason for monitoring (e.g., child safety).
- ☑️ Inform the user whenever possible and obtain consent.
- ☑️ Use reputable, transparent tools (e.g., Google Family Link, Kaspersky Safe Kids).
- ☑️ Limit access to essential data only—no invasive snooping.
- ☑️ Regularly reassess whether monitoring is still necessary.
- ☑️ Secure any collected data to prevent leaks or misuse.
Frequently Asked Questions
Can I find someone’s location using their phone’s IP address?
No, not accurately. An IP address can indicate the general area—such as a city or ISP hub—but cannot provide GPS-level precision. Accurate location tracking requires device-specific services like Find My Device or location-enabled apps.
Is it legal to monitor my spouse’s phone?
Generally, no—unless you have their informed consent. Even in marital relationships, accessing someone’s private digital data without permission may violate wiretap laws and could be used against you in legal proceedings.
Do IP-based monitoring tools exist?
Not as standalone solutions. Some network analyzers or firewall logs can record IP activity, but they are meant for IT administration, not personal surveillance. They lack context without integration into broader, authorized monitoring systems.
Conclusion
Monitoring a cell phone using its IP address is not a magic solution, nor should it be used covertly. True digital responsibility lies in balancing safety with respect for autonomy. When guided by ethics, transparency, and legality, oversight becomes a tool for protection—not control.
Whether you're a parent, employer, or caregiver, focus on building trust first. Use technology to support conversations, not replace them. By choosing integrity over intrusion, you create a safer, more respectful digital environment for everyone involved.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?