In an era where smartphones hold the keys to our digital lives—banking details, private messages, location history, photos, and more—the threat of unauthorized surveillance is no longer science fiction. Hidden spy apps can silently infiltrate your device, recording every tap, call, and movement without your knowledge. These tools, often marketed as parental control or employee monitoring software, are increasingly misused for stalking, corporate espionage, or personal invasion.
The danger lies in their stealth. Modern spyware is designed to remain invisible: no icons, no notifications, and minimal battery drain. But just because it's hidden doesn’t mean it’s undetectable. With the right awareness and techniques, you can uncover suspicious activity and reclaim your digital sovereignty.
Understanding Spy Apps: What They Can Do
Spy apps, also known as stalkerware or monitoring software, are applications that run in the background of a smartphone to collect data covertly. Depending on the sophistication, they may:
- Record calls and ambient audio
- Track real-time GPS location
- Access text messages, emails, and social media chats (including WhatsApp, Telegram, Instagram)
- Take screenshots or photos using front/rear cameras
- Monitor browsing history and keystrokes
- Upload all collected data to a remote server accessible by the attacker
These apps often require physical access to install, but some advanced variants exploit vulnerabilities via phishing links or zero-click exploits. Once installed, many operate under root or administrator privileges, making them difficult to remove.
“Most spyware today is designed to mimic system processes. The average user won’t notice anything unusual—until it’s too late.” — Dr. Lena Torres, Cybersecurity Researcher at the Digital Privacy Institute
Step-by-Step Guide to Detecting Hidden Spy Apps
Detection requires a combination of technical checks and behavioral observation. Follow these steps systematically to assess whether your phone has been compromised.
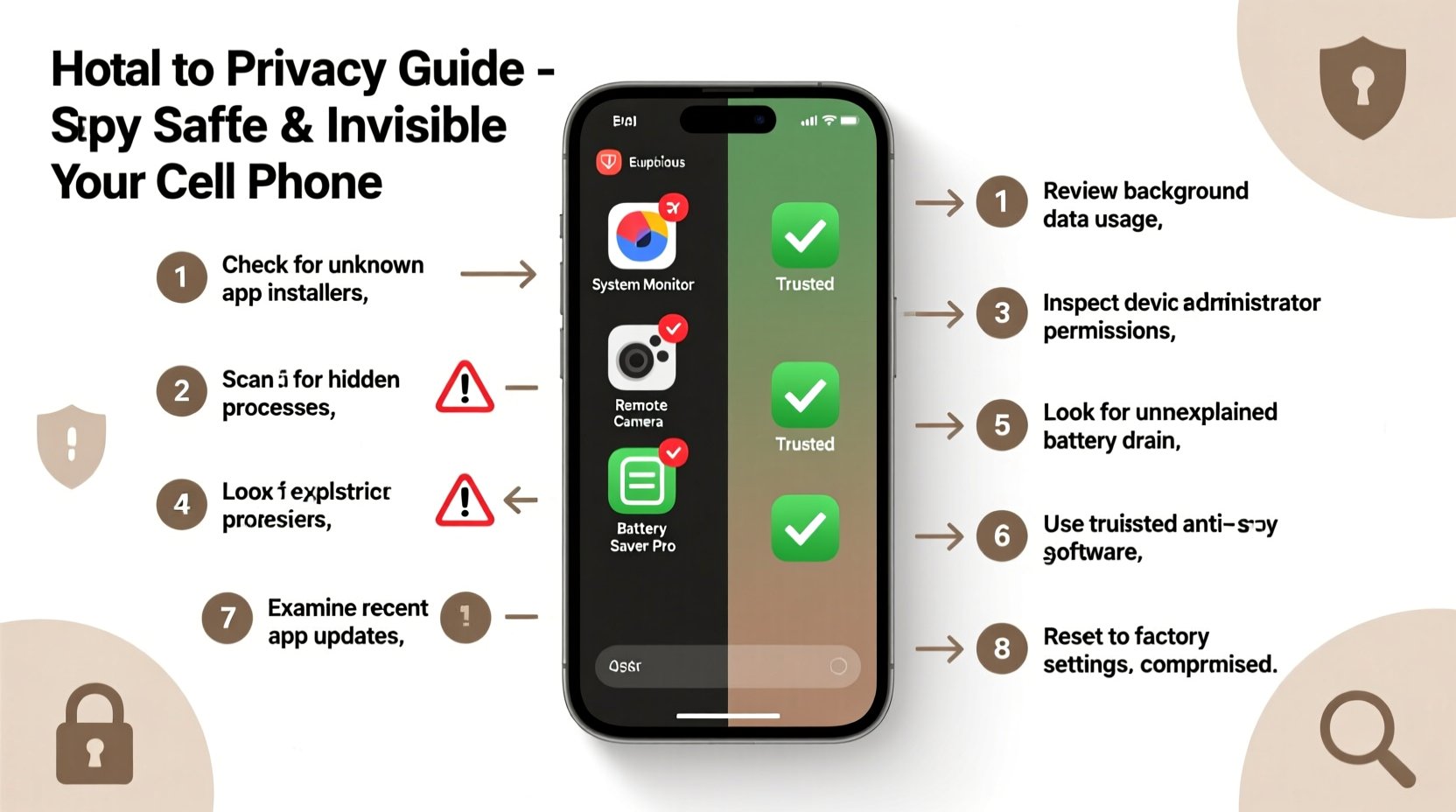
- Check for Unfamiliar Apps
Go to Settings > Apps (or Application Manager). Scroll through the list carefully. Look for apps with generic names like “System Update,” “Service Tool,” or “Device Optimization.” Some spy apps disguise themselves as Google services or battery savers. - Review App Permissions
Navigate to Settings > Privacy > Permission Manager. Pay close attention to apps with excessive permissions:- Access to SMS, Calls, Contacts, Camera, Microphone, or Location when not necessary
- Background location tracking enabled on non-location-based apps
- Look for Unknown Admin Privileges
On Android: Settings > Security > Device Administrators.
On iOS: Settings > General > VPN & Device Management.
If you see an unfamiliar profile or app listed as administrator, it could be spyware. Remove it only if you're certain—it may trigger deletion attempts or alerts to the attacker. - Monitor Battery Usage
Check Settings > Battery. An app running constantly in the background—even if hidden—will consume power. Look for unusual spikes or unknown processes draining energy overnight. - Analyze Data Usage Patterns
Go to Settings > Network & Internet > Data Usage. Identify apps sending large amounts of data unexpectedly. Spy apps frequently upload logs, audio, and video to external servers. - Watch for Overheating or Sluggish Performance
While normal aging can slow phones, sudden lag, overheating during idle use, or unexpected reboots may indicate resource-heavy surveillance software. - Inspect for Physical Tampering
Did someone have unsupervised access to your phone? A few minutes is enough to install spyware. If your passcode was shared or guessed, assume compromise until proven otherwise.
Do’s and Don’ts When Investigating Suspicious Activity
| Do’s | Don’ts |
|---|---|
| Back up important data before making changes | Don’t confront the suspected installer unless safe to do so |
| Use reputable antivirus tools like Malwarebytes or Bitdefender | Don’t download \"anti-spy\" apps from unknown sources—they may be malware |
| Update your OS and apps regularly to patch security holes | Don’t factory reset immediately—evidence may be lost |
| Enable two-factor authentication on cloud accounts | Don’t reuse passwords across devices or services |
Real Example: Recovering Control After Discovery
Jamie, a marketing professional, began noticing odd behavior on her Android phone. Her battery drained within four hours despite light use, and she’d occasionally hear faint clicking during calls. After reading about stalkerware, she checked her device administrators and found an entry labeled “Android Service Manager”—an app she didn’t recognize.
She revoked its permissions and uninstalled it, but it reappeared after a reboot. Further investigation revealed it was linked to a legitimate-looking app called “Battery Saver Pro” downloaded months earlier from a third-party site. Jamie used Malwarebytes to scan her device, which flagged the app as high-risk. She backed up her data, performed a factory reset, and restored only essential files from a clean backup. Since then, she’s adopted strict app-installation habits and enables Google Play Protect.
Her experience underscores a key truth: early detection prevents long-term exposure.
Advanced Detection Tools and Methods
For deeper analysis, consider these tools:
- NetGuard or GlassWire (Android): Monitor outgoing network traffic. Unexpected connections to foreign IP addresses may signal data exfiltration.
- ADB (Android Debug Bridge): Advanced users can connect the phone to a computer and run commands to list all running services, including hidden ones.
- iVerify (iOS): Checks for jailbreak indicators and unauthorized configuration profiles.
- Nozomi Networks or Certo Mobile Security: Professional-grade scanners that detect known spyware signatures.
Note: iOS devices are less vulnerable due to tighter sandboxing, but jailbroken iPhones or those tricked into installing enterprise certificates can still be compromised.
Frequently Asked Questions
Can spy apps work without physical access?
Most require brief physical access for installation. However, some sophisticated attacks use phishing links (e.g., fake software updates) or exploit zero-day vulnerabilities to install remotely—though these are rare and typically target high-profile individuals.
Will a factory reset remove spy apps?
In most cases, yes. A full factory reset erases all user-installed apps and data. However, if the spyware has achieved system-level persistence (e.g., via firmware modification), even a reset may not eliminate it. For maximum safety, reinstall the operating system from official sources.
How can I prevent future infections?
Practice strong digital hygiene: lock your phone with a PIN/biometric, avoid sideloading apps, keep software updated, and never share access with untrusted parties. Consider using a privacy-focused OS like GrapheneOS for enhanced protection.
Final Checklist: Securing Your Phone Against Spyware
- Review all installed apps and uninstall anything suspicious
- Check and revoke unnecessary app permissions
- Disable unknown device administrators or profiles
- Scan with a trusted mobile security app
- Monitor battery and data usage weekly
- Enable encryption and strong authentication
- Back up data securely and perform a factory reset if needed
- Stay informed about new threats and update defenses accordingly
Protect Your Digital Self
Your smartphone is more than a device—it’s an extension of your mind, relationships, and identity. Allowing silent surveillance means surrendering autonomy over your thoughts, movements, and choices. The steps outlined here aren’t just technical fixes; they’re acts of self-defense in a world where privacy is increasingly fragile.
You don’t need to live in fear, but vigilance is non-negotiable. By learning to spot the signs, using the right tools, and adopting proactive habits, you can dismantle hidden threats and fortify your digital boundaries. Start today. Your future self will thank you.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?