In an era where digital privacy is increasingly fragile, your phone number has become one of the most sensitive pieces of personal information. Once shared with an app or service, it can be used for tracking, targeted advertising, spam calls, or even social engineering attacks. While many platforms require a phone number during registration, few make it easy to remove. This guide provides a comprehensive, practical approach to reclaiming control over your contact information across major platforms.
Why Removing Your Phone Number Matters
Your phone number is often linked to multiple layers of identity verification. It’s used for two-factor authentication (2FA), password resets, and account recovery. However, this convenience comes at a cost: once compromised, attackers can hijack your accounts through SIM swapping or phishing. Even without malicious intent, companies may sell or leak your number to third parties.
Removing your number doesn’t mean abandoning security—it means rethinking how you authenticate. Many services now support authenticator apps, backup codes, or email-based verification as safer alternatives.
“Your phone number is not just a contact method—it’s a key to your digital life. Treat it like a password.” — Dr. Lisa Chen, Cybersecurity Researcher at Stanford University
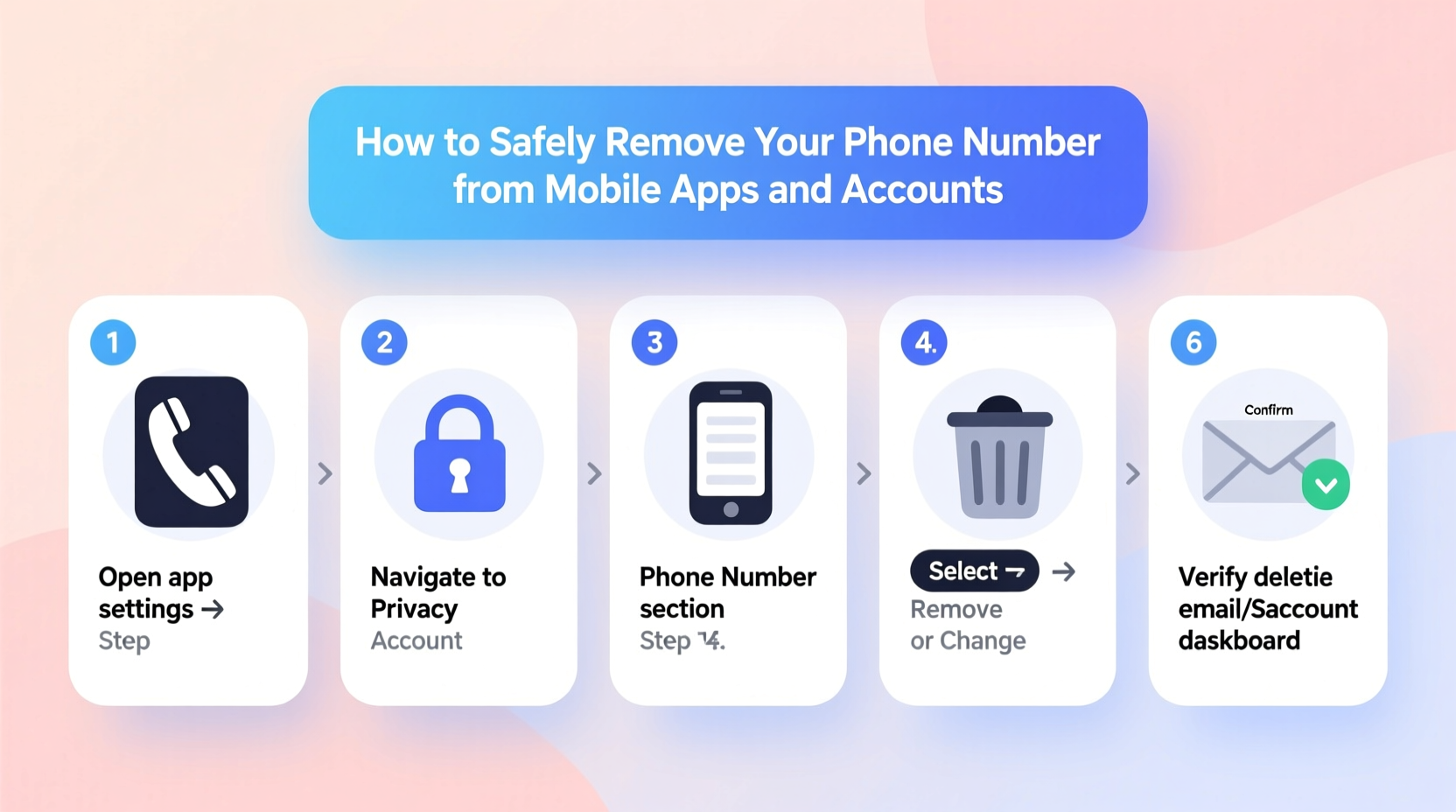
Step-by-Step Guide to Removing Your Phone Number
Follow this structured process to systematically eliminate your phone number from digital accounts while maintaining access and security.
- Audit Your Accounts: Make a list of all apps and websites where you’ve provided your number. Include social media, banking, shopping, messaging apps, and cloud storage.
- Prioritize by Risk: Rank accounts based on sensitivity. Start with high-risk platforms like email, banking, and social media.
- Set Up Alternative 2FA Methods: Before removing your number, enable authenticator apps (e.g., Google Authenticator, Authy) or generate backup codes.
- Update Account Settings: Navigate to each platform’s settings and locate the phone number field. Replace or remove it using available options.
- Test Access: After changes, log out and back in to ensure you can still access the account securely.
- Monitor for Issues: Watch for unexpected lockouts or notifications indicating failed login attempts.
Platform-Specific Removal Instructions
Not all services allow full removal of phone numbers, but most offer workarounds. Below are instructions for common platforms.
| Service | Can You Remove? | Steps |
|---|---|---|
| Google Account | Yes (with caveats) | Go to Google Account → Security → Recovery phone → Remove. Note: May require alternative recovery email or 2FA app. |
| Apple ID | Limited | Settings → [Your Name] → Password & Security → Edit Trusted Phone Number. Must have another trusted device or number. |
| Facebook / Meta | No (but hide from public) | Settings → Contact Info → Edit → Remove. Cannot fully delete if used for 2FA; replace first. |
| Twitter (X) | Yes | Settings → Privacy and Safety → Two-Factor Authentication → Switch from SMS to authenticator app, then remove number. |
| Partially | Same as Facebook. Must replace before removal. No option to leave blank permanently. | |
| No (but change number) | You cannot delete your number, but you can change it via Settings → Account → Change Number. |
What to Do When Removal Isn’t Possible
If a service refuses to let you remove your number, consider these strategies:
- Replace it with a virtual number from services like Google Voice, TextNow, or MySudo.
- Use a secondary or burner number specifically for low-trust apps.
- Contact customer support with a formal request to delete your number under data protection laws (e.g., GDPR, CCPA).
Real Example: Reclaiming Control After a Data Breach
Sophia, a freelance writer from Portland, noticed a spike in scam calls after signing up for a fitness app that required her number. She began receiving voicemails claiming she owed money and even got texts impersonating her bank. Concerned, she audited her digital footprint and found 17 active accounts linked to her personal number.
Over three weekends, Sophia replaced her number with an authenticator app on critical accounts like Gmail and her financial apps. For others, she used a Google Voice number. She also filed data deletion requests with smaller platforms under CCPA. Within a month, unsolicited calls dropped by 90%, and she regained peace of mind knowing her primary contact wasn’t exposed.
Privacy Protection Checklist
Use this checklist to ensure you’re minimizing exposure without compromising access:
- ✅ Audit all accounts with your phone number
- ✅ Enable authenticator apps for 2FA
- ✅ Generate and store backup codes securely
- ✅ Replace or remove numbers in account settings
- ✅ Request deletion under privacy laws where applicable
- ✅ Monitor accounts for unusual activity post-removal
- ✅ Avoid reusing your primary number for new signups
Frequently Asked Questions
Can I completely delete my phone number from all online accounts?
While some platforms allow full removal, others retain your number for compliance or security reasons. The goal is to minimize exposure by replacing it with safer alternatives like authenticator apps or secondary numbers.
Will removing my number disable two-factor authentication?
Only if you rely on SMS-based 2FA. Switch to an authenticator app or hardware token first. These methods are more secure than SMS and don’t require a phone number to function continuously.
What should I do if a service won’t let me remove my number?
Try replacing it with a virtual number. If that fails, submit a data deletion request under privacy regulations like GDPR (for EU residents) or CCPA (for Californians). Some companies will comply to avoid legal risk.
Final Steps Toward Digital Autonomy
Removing your phone number from digital accounts isn’t just about reducing spam—it’s a fundamental act of digital self-defense. As data brokers and automated phishing systems grow more sophisticated, every piece of personal information left unguarded becomes a potential entry point.
The steps outlined here form a sustainable privacy hygiene routine. Just as you wouldn’t reuse passwords, you shouldn’t casually hand out your primary phone number. By adopting virtual numbers, authenticator apps, and regular audits, you create layers of protection that evolve with emerging threats.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?