In today’s mobile-first world, staying charged is essential. From airports to shopping malls, public USB charging stations have become a common sight. While convenient, these ports come with a hidden danger: data exposure. Unlike standard power outlets, USB ports transfer both electricity and data. This dual function makes them vulnerable to malicious tampering—a risk known as “juice jacking.” Understanding this threat and knowing how to defend against it is critical for protecting your personal information.
Cybersecurity researchers have demonstrated that compromised charging kiosks can install malware, extract contact lists, photos, messages, or even gain full control over a connected device. The good news? With the right precautions, you can charge safely in public spaces without compromising your digital security.
Understanding the Risks of Public USB Charging
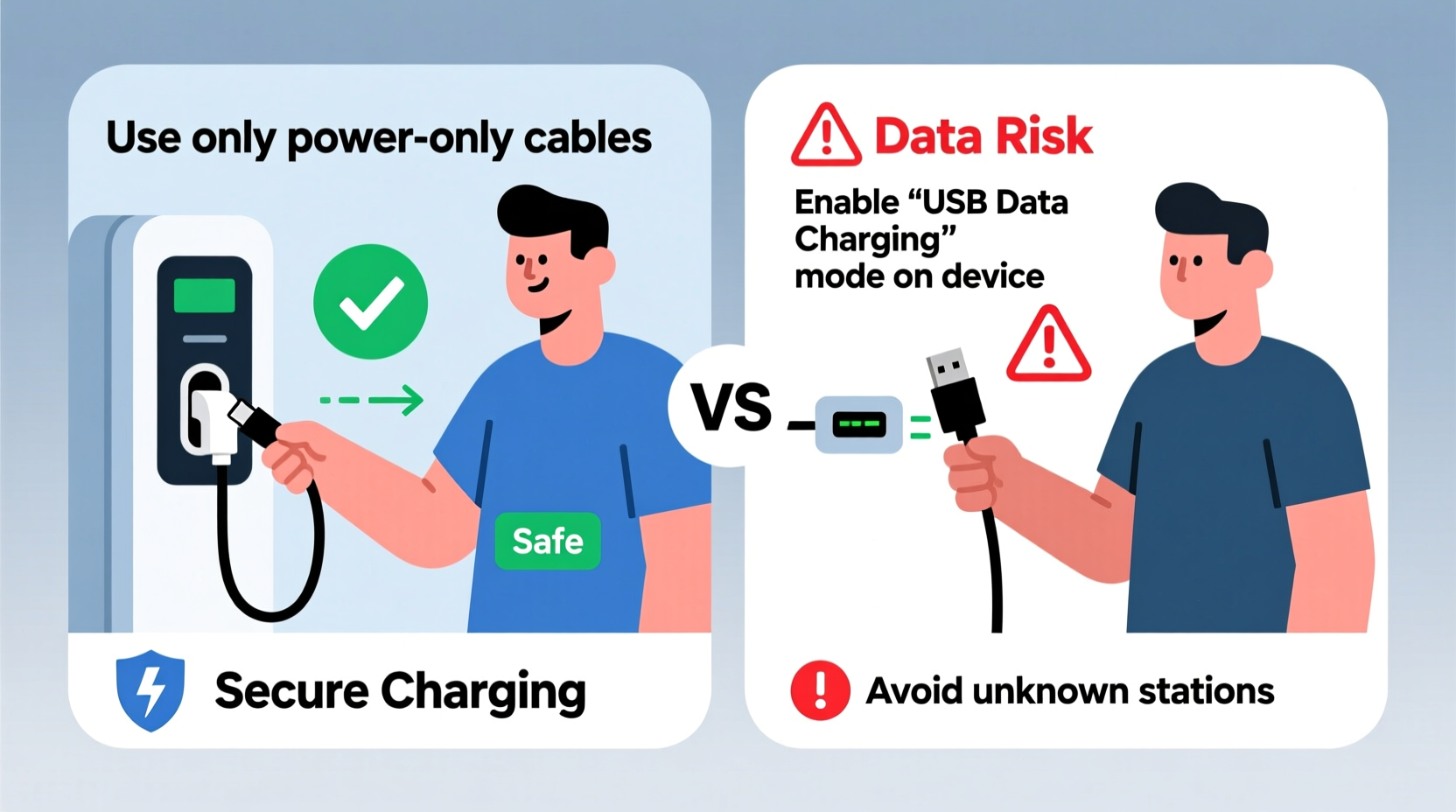
When you plug your phone into a public USB port, you’re not just drawing power—you’re establishing a two-way communication channel between your device and the host system. Most smartphones automatically attempt to establish a data connection when connected via USB, which means your device may be exposed to unauthorized access if the station has been compromised.
Juice jacking occurs when a charging station is modified to include a small computer or microcontroller capable of exploiting this data link. Once connected, the rogue device can:
- Steal stored data such as photos, messages, and contacts
- Install malware that persists after disconnection
- Log keystrokes or capture login credentials
- Pair with your device for future remote access
The Federal Trade Commission (FTC) issued a warning about juice jacking in 2019, emphasizing that while confirmed cases are rare, the technical feasibility is well-documented. As cyber threats evolve, assuming all public USB ports are safe is no longer prudent.
How to Charge Safely: A Step-by-Step Guide
Safety doesn’t mean avoiding public charging altogether. Instead, follow this sequence of actions to minimize risk while keeping your device powered.
- Assess the Charging Option: Look for AC wall outlets instead of USB ports. If only USB is available, check for signs of tampering—loose fittings, mismatched colors, or exposed wiring.
- Use Your Own Charger: Bring a compact wall charger and USB cable. Plug the charger into an AC outlet rather than using shared USB hubs.
- Enable Airplane Mode: Before plugging in, turn on airplane mode to disable Bluetooth, Wi-Fi, and cellular connections, reducing attack surfaces.
- Disable Data Transfer: On Android, tap the USB notification and select “Charge only.” On iPhone, tap “Don’t Allow” when prompted to trust the computer.
- Use a Power-Only Cable or Adapter: Invest in a data-blocker tool like a USB condom or a power-only cable that physically disables data pins.
This approach ensures that even if the port is compromised, your device remains isolated from potential threats.
Essential Tools for Secure Charging
Several affordable tools can help you maintain security while charging on the go. These products work by either blocking data transmission or eliminating reliance on public USB ports entirely.
| Tool | Function | Best For | Average Cost |
|---|---|---|---|
| USB Condom / Data Blocker | Filters out data pins; allows only power through | Travelers using public USB ports | $10–$15 |
| Power-Only USB Cable | Manufactured without data wires | Daily commuters | $8–$12 |
| Portable Power Bank | Self-contained battery; eliminates need for public charging | Frequent travelers | $25–$60 |
| Compact Wall Charger | Small AC adapter for personal use | Those with access to outlets | $15–$20 |
Among these, portable power banks offer the highest level of security and convenience. A high-capacity bank can recharge a smartphone multiple times and fits easily in a bag. Recharge it at home or in a trusted environment, ensuring you're never forced to rely on risky public infrastructure.
“Public USB ports are like public keyboards—convenient, but potentially dangerous. Assume they’re hostile until proven otherwise.” — Dr. Kevin Mitnick, former hacker and cybersecurity consultant
Real-World Example: A Traveler’s Close Call
Mark, a business consultant based in Chicago, regularly travels through O’Hare International Airport. One evening, with his phone at 3%, he plugged into a USB charging station near Gate B17. Moments later, his screen flashed a “Trust This Computer?” prompt. He instinctively tapped “Trust,” thinking it was part of normal charging.
Later that night, he noticed unfamiliar apps installed on his phone and received alerts about login attempts from unknown locations. After consulting an IT specialist, he learned that the charging kiosk had likely been tampered with. Malware had been silently installed during the brief connection, attempting to harvest his corporate email credentials.
Though the breach was contained, Mark now carries a power bank and uses a USB data blocker whenever charging in public. His experience underscores how quickly a routine action can lead to serious consequences—and how simple tools can prevent disaster.
Do’s and Don’ts of Public Charging
To reinforce best practices, here’s a clear comparison of recommended and risky behaviors.
| Do | Don't |
|---|---|
| Use your own AC charger with wall outlets | Plug directly into unsecured USB ports |
| Carry a portable power bank | Leave your device unattended while charging |
| Use a USB data blocker or power-only cable | Tap “Trust” or “Allow” on unknown prompts |
| Enable airplane mode before charging | Charge critical devices on public USB without protection |
| Inspect ports for tampering signs | Assume all charging stations are safe |
What About Wireless Charging?
Wireless charging pads, increasingly available in airports, cafes, and hotels, offer a safer alternative to USB ports. Since they transmit power via electromagnetic induction rather than a physical data connection, they eliminate the risk of juice jacking.
However, caution is still advised:
- Ensure the pad is from a reputable brand or venue.
- Avoid third-party stands with visible USB cables underneath, as they may be linked to data-collecting devices.
- Stay nearby while charging to prevent device theft.
While wireless charging isn’t foolproof—malicious firmware updates could theoretically be pushed via NFC or other protocols—it remains one of the most secure options for public power access.
FAQ: Common Questions About Public USB Safety
Can my phone be hacked just by charging?
Yes—if the USB port is compromised and your phone allows data transfer. Modern smartphones prompt you before establishing a trust relationship, but accidental taps can grant access. Using a data blocker or power-only cable prevents this risk entirely.
Are airport charging stations safe?
Major airports generally maintain secure infrastructure, but individual ports can be tampered with. High foot traffic makes them attractive targets. Even in trusted environments, it’s wise to use protective tools or avoid USB ports altogether.
Is it safe to charge my phone at a gas station?
Gas station charging stations are among the riskiest due to minimal oversight and frequent physical access. Many lack surveillance and are rarely inspected. Avoid using them unless you have a data blocker or are charging a non-sensitive device.
Protect Yourself: A Practical Checklist
Before heading out, ensure you’re prepared with this actionable checklist:
- ✅ Pack a portable power bank (fully charged)
- ✅ Bring your own wall charger and USB cable
- ✅ Purchase and carry a USB data blocker
- ✅ Enable airplane mode before connecting to any public port
- ✅ Set your phone to “Charge Only” mode (Android) or deny trust requests (iOS)
- ✅ Inspect public USB ports for damage or tampering
- ✅ Prefer wireless charging pads over USB when available
- ✅ Never leave your device unattended while charging
Conclusion: Stay Powered, Stay Protected
Public USB charging stations offer undeniable convenience, but they also introduce real cybersecurity risks. Juice jacking may not make headlines every day, but the potential consequences—data theft, identity fraud, and device compromise—are too significant to ignore. By adopting simple safeguards like using power-only cables, carrying a portable battery, and staying vigilant, you can protect yourself without sacrificing mobility.
Your smartphone holds more personal information than ever before. Treat its charging process with the same care you’d give to logging into a bank account. A few seconds of caution can prevent hours of recovery—or worse.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?