In an era where remote collaboration and digital presentations are the norm, screen mirroring has become a go-to solution for sharing content across devices. Whether you're connecting your smartphone to a smart TV, projecting a laptop to a conference room display, or using AirPlay or Chromecast, the convenience is undeniable. But when sensitive data—such as financial records, personal health information, or confidential business strategies—is involved, the question arises: Is screen mirroring truly safe?
The short answer is: not always. While screen mirroring technologies offer seamless connectivity, they also introduce potential security vulnerabilities that can be exploited if proper precautions aren’t taken. Understanding how these systems work, where the risks lie, and what safeguards exist is essential for anyone handling private or proprietary information.
How Screen Mirroring Works: A Technical Overview
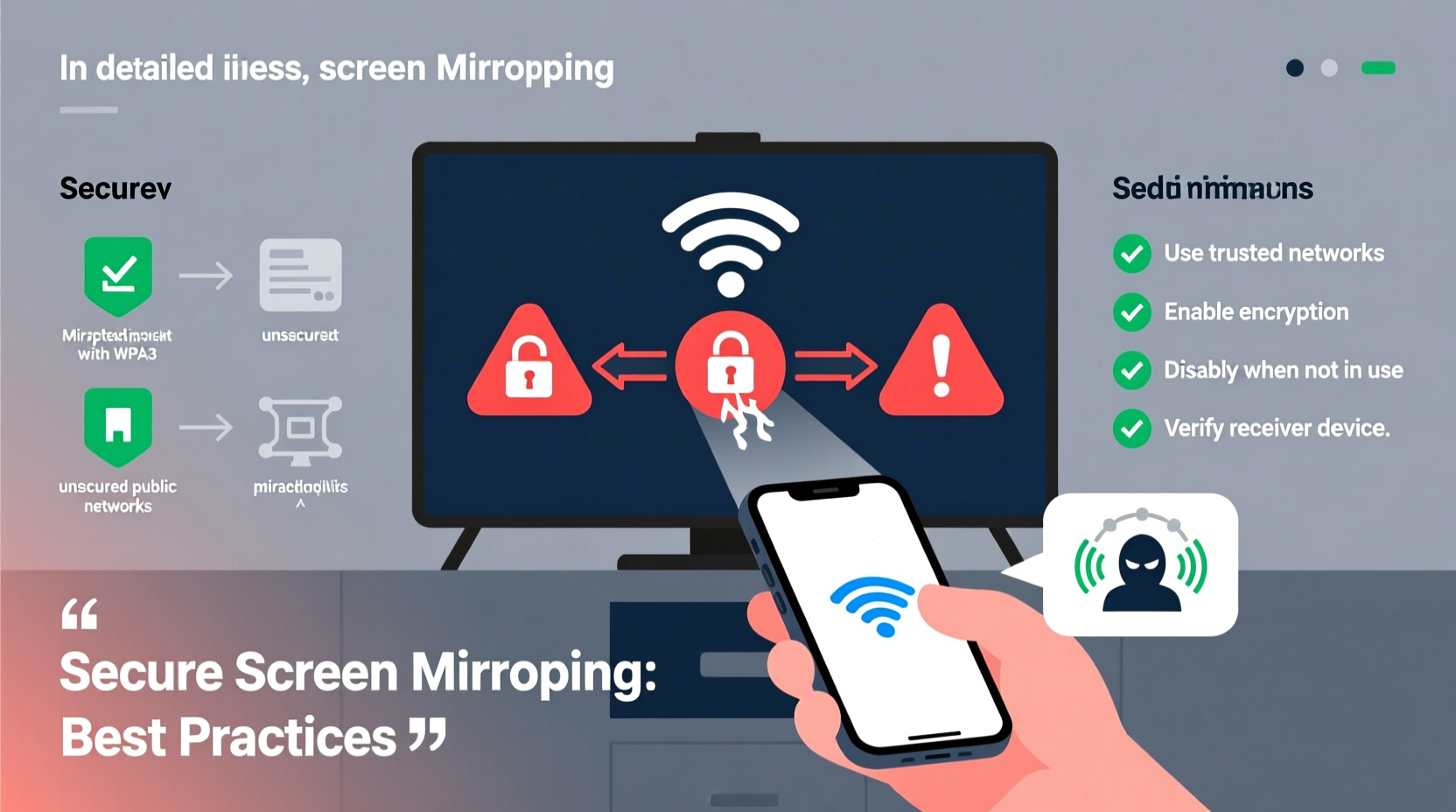
Screen mirroring relies on wireless protocols like Miracast, Apple AirPlay, Google Cast (Chromecast), or proprietary solutions such as Samsung Smart View. These technologies transmit video and audio signals from a source device (e.g., phone, tablet, laptop) to a receiver (e.g., smart TV, projector, streaming stick) over Wi-Fi or Wi-Fi Direct.
Miracast, for instance, creates a peer-to-peer connection between devices without requiring an internet-connected router. This direct link uses WPA2 encryption by default, which offers a baseline level of protection. However, not all implementations enforce strong authentication or end-to-end encryption consistently. Similarly, AirPlay encrypts streams between Apple devices, but only when both sender and receiver support modern cryptographic standards.
The core vulnerability lies in the assumption that being on the same network equates to trust. In reality, unauthorized users within range may intercept or even hijack a mirroring session if the network is poorly secured or if outdated firmware is in use.
Security Risks of Wireless Screen Mirroring
While convenient, wireless screen mirroring introduces several attack vectors that could compromise sensitive information:
- Data Interception: On unsecured or public Wi-Fi networks, attackers can capture unencrypted video streams using packet-sniffing tools.
- Unauthorized Access: Devices that auto-accept mirroring requests can be targeted by nearby hackers performing “mirroring spoofing” attacks.
- Firmware Vulnerabilities: Outdated software on TVs, projectors, or dongles may contain known exploits allowing remote code execution.
- Residual Data Exposure: Some devices temporarily store mirrored content in cache memory, potentially accessible later via physical access.
- Lack of Authentication: Many consumer-grade mirroring systems rely on simple PINs or no authentication at all, making them easy targets.
A 2022 report by cybersecurity firm Kaspersky highlighted cases where hackers used rogue Miracast emulators to trick corporate laptops into connecting and transmitting login screens and internal dashboards. In one incident, a finance team unknowingly mirrored a spreadsheet containing employee salaries during a hybrid meeting—visible to an unauthorized device connected to the same guest network.
“Wireless display technologies were designed for usability, not enterprise-grade security. Assuming they’re safe for sensitive data is a dangerous oversight.” — Dr. Lena Patel, Senior Cybersecurity Analyst at NetShield Labs
Best Practices for Secure Screen Mirroring
You don’t need to abandon screen mirroring altogether—just adopt smarter habits when dealing with confidential material. The following checklist outlines key steps to reduce risk:
✅ Secure Screen Mirroring Checklist
- Use screen mirroring only on trusted, password-protected networks (avoid public Wi-Fi).
- Ensure both sending and receiving devices have up-to-date operating systems and firmware.
- Disable automatic connection acceptance on all devices.
- Prefer protocols with built-in encryption (e.g., AirPlay with iCloud Keychain, Miracast with WPA2).
- Manually stop the mirroring session immediately after use.
- Enable two-factor authentication where available for device pairing.
- Review device logs periodically for unrecognized connection attempts.
For organizations, IT departments should consider deploying mobile device management (MDM) policies that restrict screen mirroring capabilities based on device classification (e.g., allow only on non-sensitive kiosk devices). Additionally, VLAN segmentation can isolate display devices from core internal networks to limit lateral movement in case of compromise.
Case Study: A Corporate Breach via Unsecured Mirroring
In early 2023, a mid-sized marketing agency in Chicago experienced a data leak traced back to a routine client presentation. An employee used a Chromecast-enabled conference room TV to mirror their laptop for a strategy review. Unbeknownst to them, the office’s guest Wi-Fi network had been compromised weeks earlier through a weak router password.
An external contractor working nearby discovered the open casting option and joined the session passively, viewing slides that included upcoming product launches, competitor analyses, and budget forecasts. The stream wasn’t encrypted because the Chromecast device hadn’t received a critical security update pushed six months prior. Although no credentials were exposed, the competitive intelligence gained gave a rival firm a strategic edge in a bidding war.
Post-incident, the company implemented mandatory device audits, disabled screen mirroring on guest networks, and introduced employee training on wireless sharing risks. This real-world example underscores how seemingly minor oversights can lead to significant consequences.
Comparing Screen Mirroring Protocols: Security Features at a Glance
| Protocol | Encryption | Authentication | Network Type | Recommended for Sensitive Data? |
|---|---|---|---|---|
| Miracast | WPA2 (optional) | PIN-based (varies) | Wi-Fi Direct | No (unless fully configured) |
| AirPlay (iOS/macOS) | End-to-end AES | Device trust + iCloud | Local Wi-Fi | Yes (with updated devices) |
| Google Cast | Transport-level only | Sender approval | Local Wi-Fi | Limited (avoid sensitive content) |
| Intel Wireless Display (WiDi) | WPA2 | Manual pairing | Direct or network | No (discontinued, unsupported) |
| Proprietary (e.g., Samsung Smart View) | Varies by model | App-based | Local network | Risky (verify encryption) |
This comparison shows that while some platforms offer stronger protections, none provide foolproof security out of the box. User configuration and awareness remain critical factors.
Secure Alternatives to Wireless Screen Mirroring
If you must share sensitive information visually, consider more secure methods than live wireless mirroring:
- Wired HDMI Connections: Physically connect your device using an HDMI cable. No wireless transmission means no interception risk.
- Controlled Presentation Mode: Share only specific windows or applications via conferencing tools like Zoom or Microsoft Teams instead of full-screen mirroring.
- Pre-Shared Encrypted Files: Distribute documents or slides in advance using secure file-sharing platforms (e.g., Tresorit, Proton Drive).
- Dedicated Secure Kiosks: Use air-gapped presentation devices with no network connectivity for high-stakes meetings.
- Virtual Desktop Infrastructure (VDI): Stream desktops from a secure server rather than mirroring local devices.
These alternatives trade some convenience for significantly higher security, especially important in legal, healthcare, or financial environments governed by regulations like HIPAA, GDPR, or SOX.
FAQ: Common Questions About Screen Mirroring Safety
Can someone hack my device just by connecting to my screen mirroring?
Not directly through standard mirroring alone, but if the receiving device is malicious or compromised, it could exploit vulnerabilities in the sender’s OS during negotiation. For example, flaws in Wi-Fi Direct drivers have allowed remote code execution in past CVEs (Common Vulnerabilities and Exposures).
Is it safe to mirror my phone screen during a video call?
It depends. If you’re using a trusted app like FaceTime or Zoom and only sharing the intended app window—not your entire screen—it's generally safer. However, avoid showing notifications or switching apps mid-call, as they might expose private messages or credentials.
Does turning off screen mirroring when not in use help?
Yes. Disabling features like “Allow screen mirroring” in your device settings reduces your attack surface. On Windows, disable \"Connect\" under Projecting to this PC. On Android and iOS, turn off casting options unless actively needed.
Conclusion: Proceed with Caution and Control
Screen mirroring is a powerful tool that enhances productivity and collaboration—but it was never designed as a secure channel for sensitive data. The very features that make it user-friendly—automatic discovery, minimal setup, broad compatibility—also make it inherently risky in uncontrolled environments.
Safety doesn't come from the technology itself, but from how it's used. By understanding the limitations of current protocols, applying strict configuration rules, and opting for more secure alternatives when necessary, individuals and organizations can continue leveraging wireless displays without compromising confidentiality.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?