Creating a Google account is the gateway to accessing Gmail, Google Drive, YouTube, Android services, and countless other tools that shape modern digital life. While the process is straightforward, doing it correctly—especially with security in mind—can prevent future headaches like locked accounts, data loss, or phishing attacks. This guide walks you through every stage of setting up a Google account with clarity, safety, and long-term usability as top priorities.
Why a Secure Google Account Matters
A Google account isn’t just for email. It ties together your calendar, photos, documents, app purchases, location history, and even smart home devices. If compromised, attackers could gain access to personal conversations, financial records, or private media. According to Google’s 2023 Transparency Report, over 99.7% of consumer accounts are protected from phishing and malware thanks to proactive security systems—but user behavior still plays a critical role.
“Your Google account is only as strong as its weakest link—usually an outdated password or missing recovery option.” — Dr. Lena Patel, Cybersecurity Researcher at Stanford University
Step-by-Step Guide to Creating Your Google Account
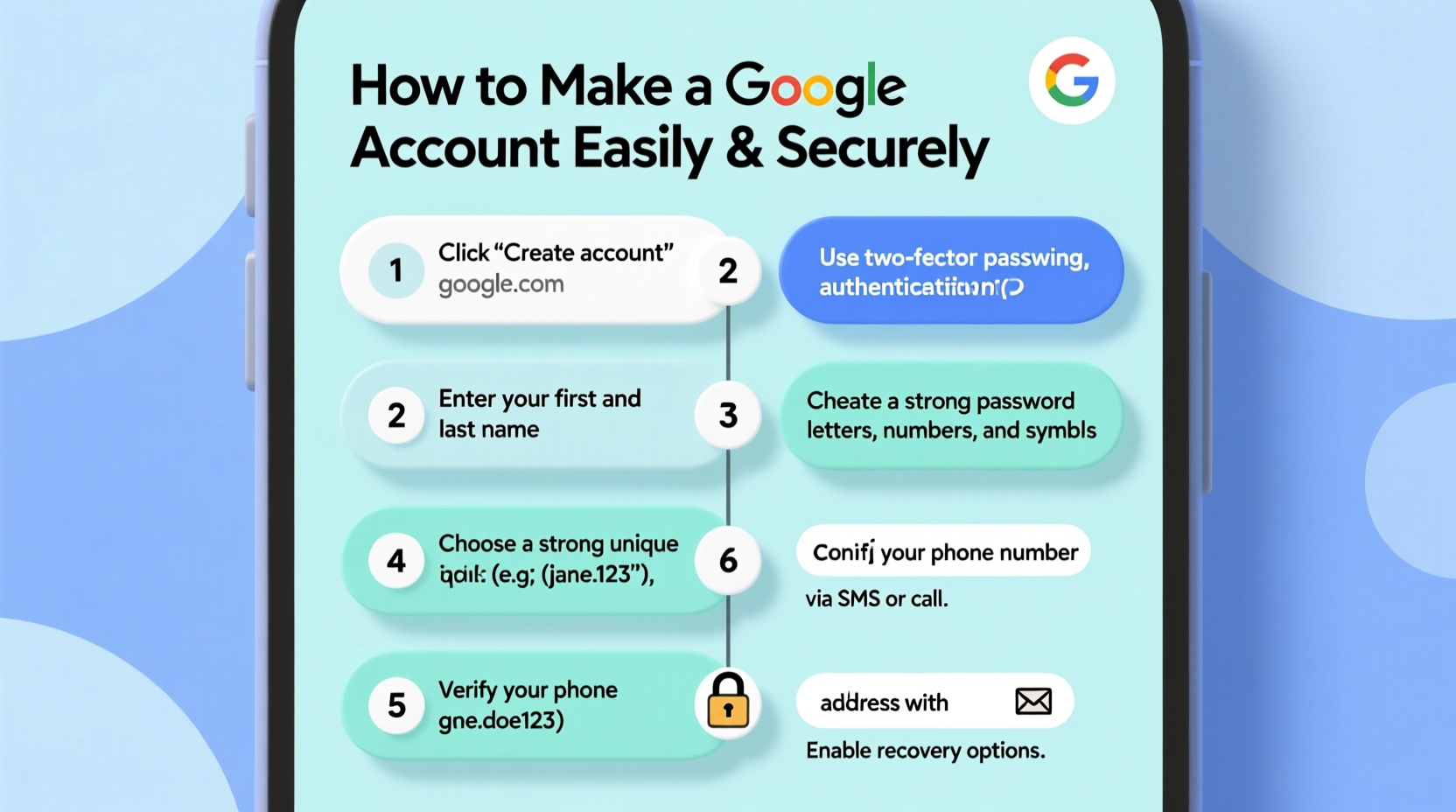
Follow this detailed sequence to set up your account from any device—desktop, laptop, tablet, or smartphone.
- Visit the Google Account Creation Page
Navigate toaccounts.google.com/signup. Avoid third-party links; always type the URL directly or search “create Google account” via trusted search engines. - Enter Your Personal Information
Fill in:- First and last name (you can use a nickname if preferred)
- The email address you want for your account (e.g., john.doe@gmail.com)
- A strong password (more on this below)
- Create a Strong Password
Use at least 12 characters combining uppercase letters, lowercase letters, numbers, and symbols. Avoid common phrases or personal info like birthdays. - Add Recovery Options
Provide either a phone number or alternate email address. Google uses these to verify identity during login issues or password resets. Choose one you control long-term. - Set Your Birthday and Gender (Optional)
This helps personalize services but doesn’t affect functionality. You may leave gender blank if desired. - Review Privacy & Terms
Read Google’s Privacy Policy and Terms of Service. While acceptance is required, understanding what data is collected—and why—empowers informed usage. - Complete Captcha Verification
Solve the puzzle or checkbox challenge to confirm you’re not a bot. - Verify Identity (If Prompted)
In some cases, Google may ask you to confirm via SMS or email. Follow instructions promptly.
Essential Security Practices After Setup
Your work doesn’t end once the account is created. The first 24 hours are crucial for locking down access and preventing future breaches.
Enable Two-Factor Authentication (2FA)
Go to Google Account > Security and turn on 2-Step Verification. You’ll be prompted for a second form of identification—like a text code, authenticator app, or physical security key—whenever logging in from a new device.
Add Backup Recovery Methods
Update both a backup phone and recovery email. If one fails, the other ensures you won’t get permanently locked out.
Review App Permissions Regularly
Third-party apps sometimes request excessive access. Check under “Third-party apps with account access” and remove anything unused or suspicious.
Turn On Google’s Advanced Protection (For High-Risk Users)
If you handle sensitive information—journalists, activists, business executives—consider enrolling in Google’s Advanced Protection Program, which requires physical security keys and blocks less secure apps by default.
Do’s and Don’ts When Setting Up a Google Account
| Do’s | Don’ts |
|---|---|
| Use a unique, complex password not shared with other sites | Reuse passwords across platforms |
| Verify your identity using a personal phone number or trusted email | Use someone else’s phone number or temporary email service |
| Store recovery codes in a safe place (password manager or printed copy) | Ignore recovery setup entirely |
| Check account activity monthly under “Security Checkup” | Click “Remember this device” on public computers |
Real Example: Recovering Access After Device Loss
Sophie, a freelance designer based in Portland, lost her phone while traveling. She couldn’t log into her laptop because 2FA was enabled. However, she had previously added a backup email and printed her Google recovery codes, stored in her travel notebook. Within minutes, she used the backup email to regain access and paused her lost device remotely via Find My Device. Her foresight saved hours of downtime and potential client delays.
This scenario underscores the importance of planning ahead. Even small precautions—like writing down recovery codes—can preserve full control when technology fails.
FAQ: Common Questions About Google Account Setup
Can I create a Google account without a phone number?
Yes, though Google strongly recommends adding one. During signup, you can skip the phone field and provide only a recovery email. Note: skipping verification may limit certain features temporarily until a method is added later.
What should I do if my desired username is taken?
Try variations: add a middle initial (jane.a.smith), use underscores (_), or include numbers related to your profession (writerjane2025). Alternatively, consider a custom domain email linked to Google Workspace for full name availability.
Is it safe to create a Google account on public Wi-Fi?
Not recommended. Public networks are vulnerable to eavesdropping. Always use a private, secured connection—or a trusted mobile hotspot—when registering sensitive accounts.
Final Checklist Before You Finish
- ✅ Chose a reliable, memorable username
- ✅ Set a strong, unique password
- ✅ Added at least one recovery method (phone or email)
- ✅ Enabled two-factor authentication
- ✅ Completed Google’s Security Checkup
- ✅ Reviewed connected devices and signed out unknown sessions
- ✅ Saved recovery codes in a secure offline location
Conclusion: Take Control of Your Digital Identity
Setting up a Google account is more than a technical task—it's the foundation of your online presence. Done carelessly, it opens doors to fraud and data loss. Done right, it becomes a secure hub for communication, creativity, and productivity. By following these steps, applying best practices, and staying vigilant, you ensure that your account remains yours alone—now and for years to come.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?