In an age where online surveillance, data harvesting, and geo-restrictions are increasingly common, many users turn to tools like VPNs and proxy servers to protect their digital footprint. Both promise anonymity and access to restricted content, but only one offers true privacy protection. Understanding the technical and practical differences between a VPN and a proxy server is essential for anyone serious about securing their internet activity.
At first glance, both tools appear similar—each routes your traffic through a remote server, masking your IP address. But beneath the surface, their architecture, security models, and impact on privacy diverge significantly. Choosing the wrong tool can leave you exposed to tracking, data theft, or even legal risk, especially when handling sensitive information or browsing in restrictive regions.
How Proxies Work—and Where They Fall Short
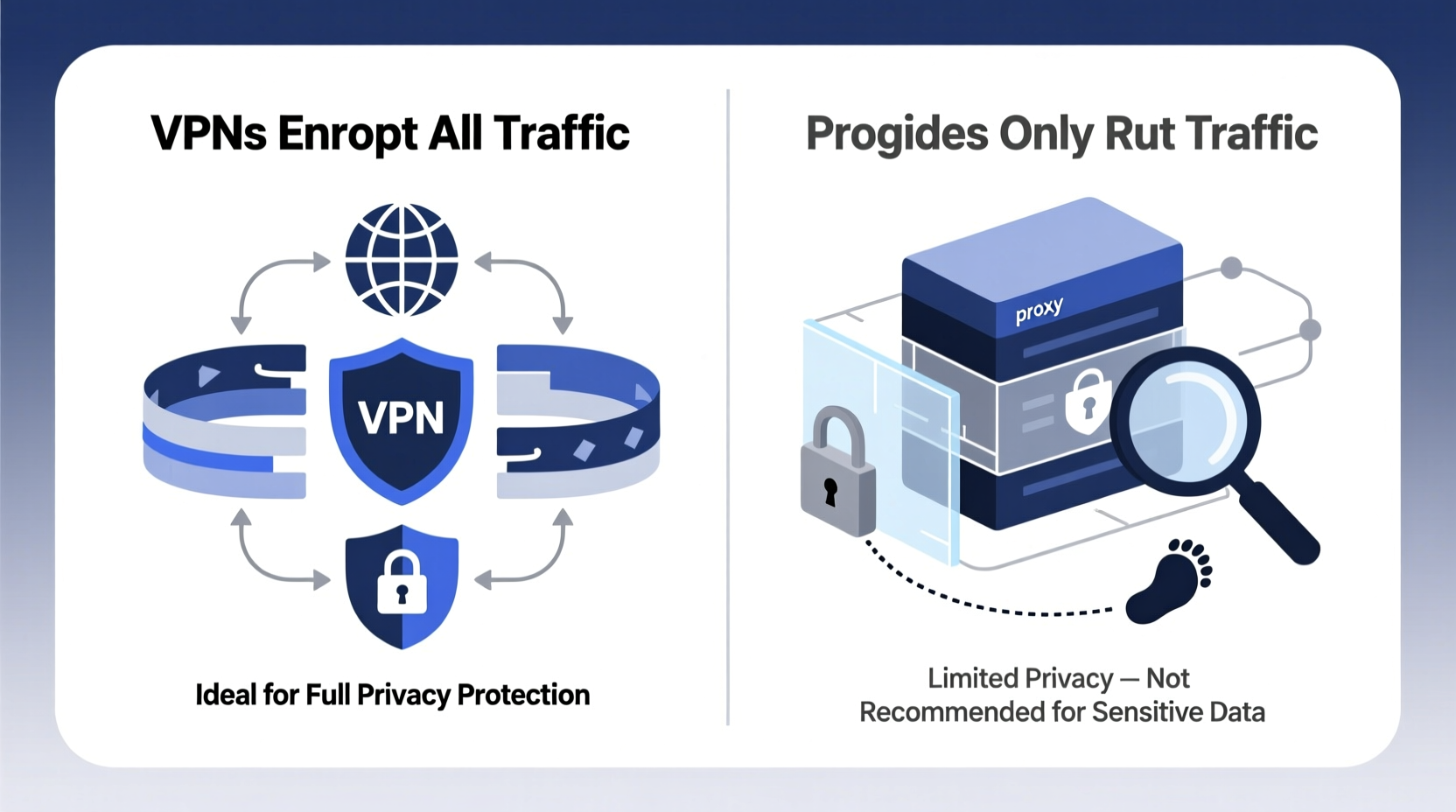
A proxy server acts as an intermediary between your device and the internet. When you connect to a website through a proxy, your request goes through the proxy server first, which then forwards it to the destination. The site sees the proxy’s IP address instead of yours, giving a basic layer of anonymity.
Proxies come in several types, including HTTP, HTTPS, and SOCKS5, each suited for different use cases:
- HTTP proxies – Best for web browsing; limited to HTTP/HTTPS traffic.
- HTTPS proxies – Support encrypted connections but only for websites using SSL/TLS.
- SOCKS5 proxies – More versatile, handling any type of traffic (e.g., torrenting, gaming), but still lack built-in encryption.
Despite their utility, proxies do not encrypt your data. This means that while your IP may be hidden from the destination site, your internet service provider (ISP), network administrator, or a malicious actor on public Wi-Fi can still intercept and read your traffic. There’s no end-to-end protection—only rerouting.
“Proxies offer obfuscation, not security. If you're transmitting login credentials or personal data over a proxy, you're essentially sending it in plain sight.” — Daniel Reyes, Cybersecurity Analyst at NetShield Labs
Why a VPN Provides Real Privacy Protection
A Virtual Private Network (VPN) does far more than just mask your IP address. It creates an encrypted tunnel between your device and the VPN server, ensuring that all data passing through—whether you’re browsing, streaming, or downloading—is protected from eavesdropping.
This encryption uses strong protocols such as OpenVPN, WireGuard, or IKEv2, which scramble your data so thoroughly that even if intercepted, it cannot be deciphered without the decryption key. Your ISP sees only that you’re connected to a VPN, not what sites you visit or what content you access.
Additionally, reputable VPN providers follow strict no-logs policies, meaning they don’t store records of your online activity. This ensures that even under legal pressure, there’s no data to hand over. In contrast, many proxy services—especially free ones—log user data and may sell it to third parties.
The comprehensive nature of a VPN makes it suitable for high-stakes scenarios: journalists communicating in repressive regimes, remote workers accessing corporate networks, or travelers avoiding location-based price discrimination.
Key Differences: A Direct Comparison
| Feature | VPN | Proxy Server |
|---|---|---|
| Data Encryption | Yes (end-to-end) | No (except HTTPS traffic) |
| IP Masking | Yes (full connection) | Yes (per application or session) |
| Traffic Coverage | All device traffic | Per-app or browser-only |
| Logging Practices | Often no-logs (if reputable) | Frequently logs user data |
| Speed Impact | Moderate (due to encryption) | Low to moderate |
| Security on Public Wi-Fi | Highly secure | Not secure |
| Use Case | Privacy, security, bypassing censorship | Bypassing geo-blocks, scraping, simple anonymity |
This comparison reveals a critical truth: proxies are tools for circumvention, not privacy. They might help you access a region-locked video or scrape a website without revealing your IP, but they do nothing to shield your data from interception or long-term tracking.
Real-World Scenario: Traveler’s Dilemma
Consider Maria, a freelance journalist traveling in a country with heavy internet censorship and active surveillance. She needs to communicate securely with her editor and access international news sources without risking exposure.
She initially tries using a free web proxy to access blocked sites. While it works briefly, she notices that some pages fail to load, and her login sessions keep timing out. Worse, after a few days, she receives suspicious emails referencing her recent searches—indicating someone is monitoring her activity.
Switching to a trusted paid VPN, she immediately notices a difference. All sites load normally, her connection remains stable, and she can use encrypted messaging apps without fear. The encryption prevents local ISPs from seeing her traffic, and the no-logs policy ensures her activity isn’t stored. Her digital safety improves dramatically—not because her IP is hidden, but because her entire connection is secured.
This case illustrates that privacy isn’t just about hiding your location. It’s about controlling who can see, collect, and exploit your data.
Common Misconceptions About Proxies and VPNs
Many users believe that because a proxy hides their IP, it provides full anonymity. This is a dangerous misconception. Anonymity without encryption is fragile. Your ISP, employer, or government agency can still detect patterns in your usage, such as the volume and timing of data transfers, which can be used to de-anonymize you.
Another myth is that “free” equals “safe.” Free proxies and even some free VPNs often monetize user data. Research has shown that a significant number of free Android VPN apps contain malware or trackers. One study by the Commonwealth Scientific and Industrial Research Organisation (CSIRO) found that 38% of free Android VPNs had privacy-compromising behaviors, including injecting ads and leaking user data.
True privacy requires investment—either in time (configuring open-source tools) or money (subscribing to reputable services). If you’re not paying for the product, you’re likely the product.
Choosing the Right Tool: A Practical Checklist
Before deciding between a proxy and a VPN, ask yourself the following questions. Use this checklist to guide your decision:
- Am I transmitting sensitive data? – If yes (e.g., passwords, messages, financial info), use a VPN.
- Do I need full-device protection? – If yes (e.g., securing all apps), a VPN is required.
- Is speed my top priority? – Proxies are faster for simple tasks, but not secure.
- Am I in a high-risk environment? – Journalists, activists, or business travelers should always use a VPN.
- Do I trust the service provider? – Check independent audits, jurisdiction, and logging policies.
- Is the service free? – Be cautious. Free services often have hidden costs in privacy.
When a Proxy Might Be Acceptable
There are niche situations where a proxy is sufficient and even preferable:
- Web scraping – Rotating proxies allow bots to avoid IP bans without needing encryption.
- Quick geo-unblocking – For temporarily accessing a region-locked article or video.
- Testing website appearance – Developers use proxies to view sites from different locations.
Even in these cases, HTTPS or SOCKS5 proxies are recommended over HTTP for better security. However, never rely on them for anything beyond short-term, low-risk tasks.
FAQ: Common Questions Answered
Can a proxy hide my identity completely?
No. While a proxy masks your IP address from the destination server, it doesn’t encrypt your traffic. Your ISP, network administrator, or hackers on shared networks can still see what you’re doing online. True identity protection requires encryption, which proxies lack.
Are all VPNs safe for privacy?
Not all. Some VPNs log user activity, operate in countries with invasive surveillance laws, or contain vulnerabilities. Choose a provider with a proven no-logs policy, strong encryption standards, and third-party security audits. Avoid unknown or free services with unclear ownership.
Does a VPN slow down my internet more than a proxy?
Generally, yes—because encryption takes processing power. However, modern protocols like WireGuard minimize speed loss. The trade-off is worth it for the level of security gained. Proxies are faster but offer no real protection.
Conclusion: Privacy Isn’t Optional—Choose Wisely
The choice between a proxy and a VPN isn't just technical—it's ethical and personal. Your online activity reflects your interests, beliefs, and relationships. Letting that data flow unencrypted across networks is akin to having private conversations in a crowded room.
If your goal is convenience or temporary access, a proxy might suffice. But if you value your privacy, security, and autonomy online, a reputable VPN is non-negotiable. It’s the only tool that combines IP masking with military-grade encryption, full-system coverage, and accountability through transparent policies.
Don’t gamble with your digital life. Audit your current setup. Are you truly protected, or just rerouted? Upgrade to a trusted VPN service today, enable the kill switch, and browse knowing your data stays yours.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?