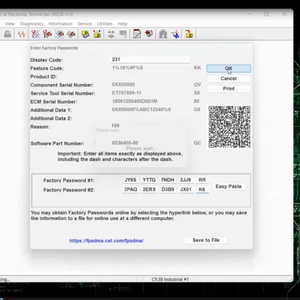
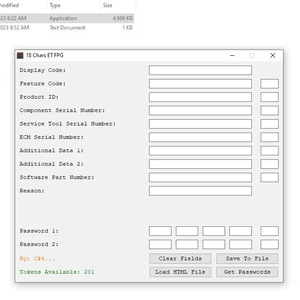
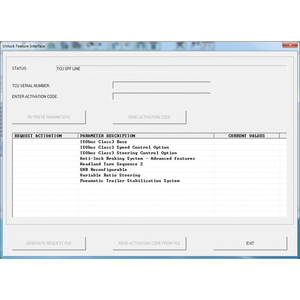
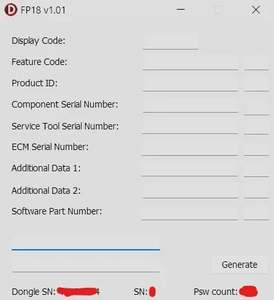
Secure Password Maker



 1/3
1/3



 0
0




 1/3
1/3





 1/3
1/3




 1/3
1/3



 1/1
1/1




 1/3
1/3





 1/3
1/3








 1/21
1/21



 0
0







 1/11
1/11





 1/3
1/3



 0
0





 1/3
1/3




 1/3
1/3



 0
0






 1/32
1/32





 1/3
1/3



 0
0



 1/3
1/3
About secure password maker
Where to Find Secure Password Maker Suppliers?
No verified suppliers for secure password makers are currently available in major manufacturing hubs. Unlike industrial machinery categories with established production clusters, the secure password maker segment lacks dedicated physical manufacturing ecosystems. These digital tools are typically developed by software firms or integrated into cybersecurity platforms rather than produced as standalone hardware devices in traditional factory settings.
As a result, economies of scale, vertical integration, and regional supply chain advantages observed in heavy equipment manufacturing do not apply. The absence of specialized industrial zones means buyers must focus on technical validation and digital service delivery capabilities rather than facility size, component proximity, or logistics infrastructure. Lead times and production volumes are therefore less predictable and often dependent on software development cycles rather than material sourcing or assembly line capacity.
How to Choose Secure Password Maker Suppliers?
Prioritize these verification protocols when selecting partners:
Technical Compliance
Require evidence of adherence to recognized cybersecurity standards such as ISO/IEC 27001, NIST SP 800-63, or FIPS 140-2 where applicable. Confirm encryption protocols (e.g., AES-256, PBKDF2, bcrypt) used in password generation and storage. For enterprise integration, verify compatibility with SAML, OAuth 2.0, or OpenID Connect frameworks.
Development Capability Assessment
Evaluate technical infrastructure and team expertise:
- Minimum two years of documented experience in cryptographic software development
- Demonstrated use of secure coding practices and regular third-party penetration testing
- Version control transparency and update frequency logs
Cross-reference code audit reports with deployment history to assess long-term reliability and vulnerability management.
Transaction Safeguards
Implement phased payment structures tied to milestone deliveries, especially for custom integrations. Request access to sandbox environments for functional testing prior to full deployment. Verify data jurisdiction compliance—particularly GDPR, CCPA, or HIPAA—depending on end-user location. Source code escrow agreements are recommended for mission-critical applications to ensure continuity.
What Are the Best Secure Password Maker Suppliers?
No supplier data is currently available for secure password maker providers. The absence of structured company profiles—including operational tenure, staff composition, facility details, delivery performance, or customer ratings—limits objective comparison. Buyers should rely on independent security audits, peer-reviewed algorithm implementations, and open-source community contributions as proxy indicators of product integrity and developer credibility.
Performance Analysis
Without quantifiable supplier metrics, procurement decisions must emphasize technical due diligence over operational KPIs. Preference should be given to vendors who publish detailed threat models, maintain public bug bounty programs, or contribute to standardized cryptographic libraries. Open APIs, documentation quality, and backward compatibility serve as key differentiators in assessing long-term viability and integration flexibility.
FAQs
How to verify secure password maker supplier reliability?
Review published whitepapers, cryptographic design choices, and third-party audit results from accredited firms. Check participation in industry forums such as OWASP or IETF. Validate claims through independent red-team assessments or automated vulnerability scanning tools before adoption.
What is the average sampling timeline?
Functional demonstrations or trial versions are typically available within 1–3 business days. Full API access or sandbox provisioning may require identity verification and legal onboarding, extending setup to 5–7 days. Custom feature development cycles range from 2 to 6 weeks depending on complexity.
Can suppliers ship secure password maker solutions worldwide?
Yes, digital distribution enables global deployment. However, compliance with local data protection laws must be confirmed. Some jurisdictions restrict cross-border transfer of authentication data or mandate local data residency. Ensure encryption policies align with national regulations before implementation.
Do manufacturers provide free samples?
Most providers offer free-tier access or time-limited trials for evaluation. Feature-restricted versions allow testing core functionality at no cost. Full commercial licensing typically begins after proof-of-concept validation, with pricing based on user count, API call volume, or deployment scope.
How to initiate customization requests?
Submit detailed requirements including entropy sources, character set constraints, length parameters, and export format (JSON, CSV, etc.). Specify integration needs such as browser extension support, mobile SDKs, or enterprise directory synchronization. Reputable developers will respond with architecture proposals within 5 business days and deliver test builds in 3–4 weeks.