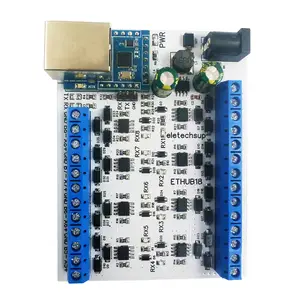
Tcp Port No









 1/52
1/52

 CN
CN











 1/3
1/3




 0
0




 1/3
1/3




 1/3
1/3


 0
0




 1/3
1/3




 1/3
1/3




 1/3
1/3








 0
0










 1/3
1/3




 1/3
1/3







 1/8
1/8



 1/1
1/1




 1/3
1/3




 1/2
1/2



 1/3
1/3
About tcp port no
Where to Find TCP Port Number Suppliers?
The term “TCP port number” does not refer to a physical product, component, or manufactured good—it is a conceptual, protocol-level identifier defined within the Internet Protocol (IP) suite. As such, there are no industrial suppliers, factories, or sourcing ecosystems producing or distributing “TCP port numbers” as tangible items. TCP port numbers (ranging from 0–65535) are standardized numerical identifiers assigned by the Internet Assigned Numbers Authority (IANA) and implemented in software stacks, operating systems, networking devices, and application-layer services.
Procurement professionals seeking infrastructure or services related to TCP port management—such as firewalls, load balancers, network address translation (NAT) appliances, or embedded communication modules—must instead evaluate suppliers of networking hardware, firmware-enabled edge devices, or enterprise-grade software platforms. These vendors implement port assignment logic per RFC 793 (Transmission Control Protocol) and adhere to IANA’s Service Name and Transport Protocol Port Number Registry. No supplier manufactures, stocks, or ships “port numbers” as discrete SKUs.
How to Choose Suppliers for TCP-Enabled Networking Equipment?
When sourcing hardware or software solutions requiring precise TCP port configuration, verification must focus on technical implementation fidelity—not physical supply chain attributes. Prioritize these criteria:
Standards Compliance
Verify conformance with foundational IETF specifications: RFC 793 (TCP), RFC 1700 (now superseded but historically referenced for port assignments), and current IANA port registry alignment. For regulated environments (e.g., healthcare, finance), confirm adherence to NIST SP 800-41 Rev. 2 (Guidelines on Firewalls and Firewall Policy) and ISO/IEC 27001 controls for network segmentation.
Implementation Capability Assessment
Evaluate vendor documentation and architecture:
- Support for dynamic port allocation (ephemeral range: 49152–65535 per RFC 6056)
- Configurable static port binding for well-known services (e.g., port 80/HTTP, 443/HTTPS, 22/SSH)
- Stateful packet inspection (SPI) capability to enforce port-based access control lists (ACLs)
- Validation of port exhaustion mitigation (e.g., TIME_WAIT tuning, connection reuse)
Operational Safeguards
Require evidence of production-ready port-handling behavior:
- Independent third-party security assessments (e.g., Common Criteria EAL2+ for network gateways)
- Public vulnerability disclosure records confirming prompt remediation of port-related flaws (e.g., CVE-2023-27997 in legacy TCP stack implementations)
- Documentation of default port lockdown policies (e.g., closed-by-default ephemeral ports, disabled unused services)
What Are the Key Suppliers for TCP-Port-Capable Infrastructure?
| Vendor Category | Core Capabilities | Standards Alignment | Typical Lead Time | MOQ | Customization Scope | Export Experience | Quality Certifications |
|---|---|---|---|---|---|---|---|
| Enterprise Firewall OEMs | Stateful inspection, port forwarding/NAT, application-aware filtering | RFC 793, RFC 6056, IANA port registry | 4–8 weeks (hardware); 1–3 days (firmware updates) | 1 unit (evaluation); ≥10 units (volume pricing) | Firmware-level port mapping rules, custom ACL syntax, API-driven policy deployment | Global distribution via certified channel partners; CE, FCC, RCM, KC certifications maintained | ISO 9001, ISO/IEC 27001, Common Criteria certified platforms |
| Industrial IoT Gateway Manufacturers | Modbus/TCP bridging, TLS-encrypted port tunneling, configurable listen ports | RFC 793, RFC 5246 (TLS), IEC 62443-4-2 | 6–12 weeks (custom firmware variants); 2–4 weeks (standard models) | 5 units (minimum for firmware customization) | Custom port ranges per protocol stack, certificate-based port binding, zero-trust port authorization | Export-compliant firmware builds (EAR99); regional certifications (UL 62368-1, EN 61000-6-4) | ISO 9001, ISO 13485 (for medical-adjacent deployments), IECQ QC 080000 (RoHS) |
| Network Equipment ASIC Providers | Hardware-accelerated TCP offload (TOE), port-based QoS scheduling, deep packet inspection engines | RFC 793, RFC 1122, IEEE 802.1Qbv (time-aware shaping) | 16–24 weeks (ASIC tape-out + validation); reference design kits available immediately | NRE fees apply; volume MOQ ≥50k units | RTL-level port state machine customization, dedicated port counters, programmable port thresholds | Global wafer fabrication & packaging; ITAR-free designs; export licenses managed per destination | ISO 9001, IATF 16949 (for automotive-grade silicon), AEC-Q200 qualified components |
Performance Analysis
Enterprise firewall OEMs deliver the highest operational readiness for port-centric use cases, with pre-validated ACL rule sets and automated port conflict detection. Industrial gateway vendors provide critical flexibility for legacy protocol integration but require rigorous firmware validation to prevent port starvation under high-concurrency loads. ASIC providers enable deterministic port handling at line rate but demand significant engineering investment—only justified for deployments exceeding 100k units annually. All categories require formal validation of port exhaustion recovery behavior (e.g., kernel parameter tuning, socket reuse enforcement) prior to deployment.
FAQs
Can TCP port numbers be purchased or licensed?
No. TCP port numbers are not proprietary assets, commodities, or intellectual property. They are publicly documented, vendor-neutral identifiers governed by IANA. No entity sells, leases, or assigns exclusive rights to port numbers. Commercial vendors may bundle port configuration support as part of service contracts—but the port numbers themselves remain freely usable per RFC standards.
What is the typical lead time for custom TCP port configuration support?
Standard configuration (e.g., port forwarding rules, firewall ACLs) is delivered immediately via CLI/GUI. Custom firmware modifications—including non-standard port binding logic or proprietary port multiplexing—require 4–12 weeks depending on vendor validation cycles. Third-party integrators typically add 2–3 weeks for end-to-end testing.
Do suppliers guarantee port availability or collision avoidance?
No supplier guarantees global port uniqueness. Collision avoidance is enforced locally: operating systems manage ephemeral port allocation via algorithms compliant with RFC 6056; network devices enforce port-based policies per configured ACLs. Vendors document their implementation’s adherence to TIME_WAIT handling, port reuse semantics (SO_REUSEADDR), and randomization entropy—but cannot prevent collisions across independently administered networks.
How to verify TCP port implementation quality?
Validate using standardized test suites: iPerf3 for throughput under port-constrained conditions, ss -tuln for local port state visibility, Wireshark captures to confirm SYN/ACK sequence integrity, and nmap -sS scans to verify external port exposure. Cross-reference vendor test reports against RFC 793 Section 3.7 (Connection Establishment and Clearing) and RFC 6056 Section 3 (Ephemeral Port Selection).
Are there regulatory restrictions on TCP port usage?
While port numbers themselves are unrestricted, certain jurisdictions regulate services bound to specific ports. Examples include GDPR-aligned data flows over port 443, HIPAA-covered entity requirements for TLS 1.2+ on port 443, and China’s MIIT regulations mandating registration of public-facing services on ports 80/443. Suppliers must provide documentation demonstrating compliance with applicable jurisdictional service-layer regulations—not port number allocation.