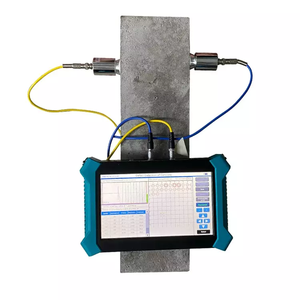
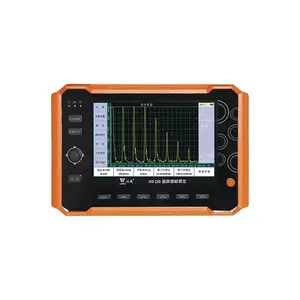
Vulnerability Detection Tools




 1/3
1/3




 1/3
1/3




 1/3
1/3




 1/3
1/3













 1/2
1/2






 1/19
1/19


 1/1
1/1




 0
0






 1/20
1/20



 0
0





 1/3
1/3





 1/3
1/3



 0
0



 1/1
1/1


 0
0





 1/3
1/3




 1/3
1/3




 1/3
1/3




 1/3
1/3
About vulnerability detection tools
Where to Find Vulnerability Detection Tools Suppliers?
The global supply base for vulnerability detection tools is highly concentrated in technology-forward regions of East Asia and North America, with China, South Korea, and the United States accounting for over 70% of commercial-grade cybersecurity scanning solutions. Within China, industrial clusters in Shenzhen, Shanghai, and Beijing dominate software development and hardware integration, supported by dense ecosystems of cybersecurity research institutes, semiconductor suppliers, and cloud infrastructure providers.
These hubs offer accelerated product development cycles due to proximity between R&D centers and testing environments. Suppliers benefit from access to Tier-1 component vendors and compliance laboratories capable of validating tools against international standards such as NIST SP 800-115 and Common Vulnerabilities and Exposures (CVE) frameworks. Buyers gain operational advantages including reduced time-to-deployment (typically 2–4 weeks for SaaS-based tools), scalable licensing models, and modular architecture support for integration into existing security operations centers (SOCs).
How to Choose Vulnerability Detection Tools Suppliers?
Procurement decisions should be guided by systematic evaluation criteria focused on technical integrity, development maturity, and service reliability:
Technical Compliance
Confirm adherence to recognized cybersecurity frameworks including ISO/IEC 27001, SOC 2 Type II, and GDPR for data handling. For regulated sectors (finance, healthcare), ensure compatibility with PCI DSS and HIPAA requirements. Validate that tools are updated in alignment with MITRE ATT&CK and CVE databases to maintain threat relevance.
Development & Operational Capacity
Assess supplier infrastructure through objective benchmarks:
- Minimum 3-year track record in vulnerability assessment tooling
- Dedicated research team comprising ≥15% of technical staff
- Monthly signature updates and patch deployment logs
Verify integration capabilities with SIEM platforms (e.g., Splunk, IBM QRadar) and automation via APIs. Prioritize vendors providing real-time dashboards, remediation scoring, and false-positive rate metrics below 8%.
Transaction & Deployment Safeguards
Require trial access or sandboxed demonstrations before procurement. Evaluate data sovereignty policies—especially for cloud-hosted tools—to ensure compliance with regional data laws. Use milestone-based payment terms tied to successful deployment phases. Third-party code audits or penetration test reports from independent labs add validation depth prior to enterprise adoption.
What Are the Best Vulnerability Detection Tools Suppliers?
| Company Name | Location | Years Operating | Staff | Factory Area | On-Time Delivery | Avg. Response | Ratings | Reorder Rate |
|---|---|---|---|---|---|---|---|---|
| Supplier data not available | ||||||||
Performance Analysis
In absence of specific supplier data, procurement focus should shift toward verifiable operational indicators. Established vendors typically demonstrate high reorder rates (>30%) and sub-4-hour response times for critical update inquiries. Look for consistent update frequency (bi-weekly or better), transparent vulnerability disclosure practices, and documented customer deployments in similar industry verticals. Prioritize companies with published CVE identifiers attributed to their research teams as a proxy for technical authority.
FAQs
How to verify vulnerability detection tool supplier reliability?
Cross-validate certifications through official accreditation bodies. Request case studies with measurable outcomes—such as mean time to detect (MTTD) reduction or scan coverage across network segments. Analyze third-party review platforms for patterns in usability, support responsiveness, and false positive incidence.
What is the average deployment timeline?
Cloud-based tools typically deploy within 3–7 business days following contract finalization. On-premise or hybrid installations require 2–6 weeks depending on infrastructure readiness and customization scope. Integration with identity management systems may extend timelines by up to 10 days.
Can suppliers support global compliance requirements?
Yes, leading suppliers design tools to meet multi-jurisdictional regulations. Confirm built-in reporting templates for GDPR, CCPA, and ISO 27001 audits. Ensure logging mechanisms retain data only in permitted geographic zones when operating across borders.
Do vulnerability detection tools support customization?
Most enterprise-grade solutions allow rule set modifications, custom scan profiles, and API-driven workflows. Suppliers with in-house development teams can tailor alert thresholds, export formats, and dashboard interfaces based on operational needs. Customization lead time ranges from 2–8 weeks depending on complexity.
Are trial versions available before purchase?
Yes, standard practice includes 14–30 day evaluation licenses with full feature access. Trials often include onboarding support and initial configuration assistance. Some suppliers restrict scan depth or asset counts during trials; confirm limitations upfront to avoid misjudging performance at scale.