In an age where smartphones store everything from private messages and photos to banking details and location history, ensuring complete data removal before parting with your device is not just prudent—it’s essential. A factory reset may seem sufficient, but residual data can often be recovered with the right tools. Whether you're upgrading, selling, or recycling your phone, truly erasing your digital footprint requires a more deliberate approach.
Understanding how data persists—even after deletion—and knowing the correct procedures can protect you from identity theft, privacy breaches, and unauthorized access. This guide outlines proven, step-by-step methods to ensure every trace of your personal information is permanently removed from your mobile device.
Why a Factory Reset Isn’t Enough
Most users assume that performing a factory reset on their smartphone wipes all data. While this action removes visible files and settings, it doesn't always overwrite the underlying data stored in the phone’s memory. Instead, the operating system simply marks the space as available for new data. Until that space is overwritten, skilled individuals using data recovery software can retrieve old messages, photos, contacts, and even passwords.
This is especially true for older Android devices that don’t use file-based encryption by default. Even on newer phones with encryption, if the encryption key isn’t properly destroyed during reset, data may still be recoverable under certain forensic conditions.
“Many people believe their data is gone after a reset. In reality, it's like shredding a document into large pieces—still reconstructible.” — Dr. Lena Torres, Digital Forensics Researcher at SecureData Lab
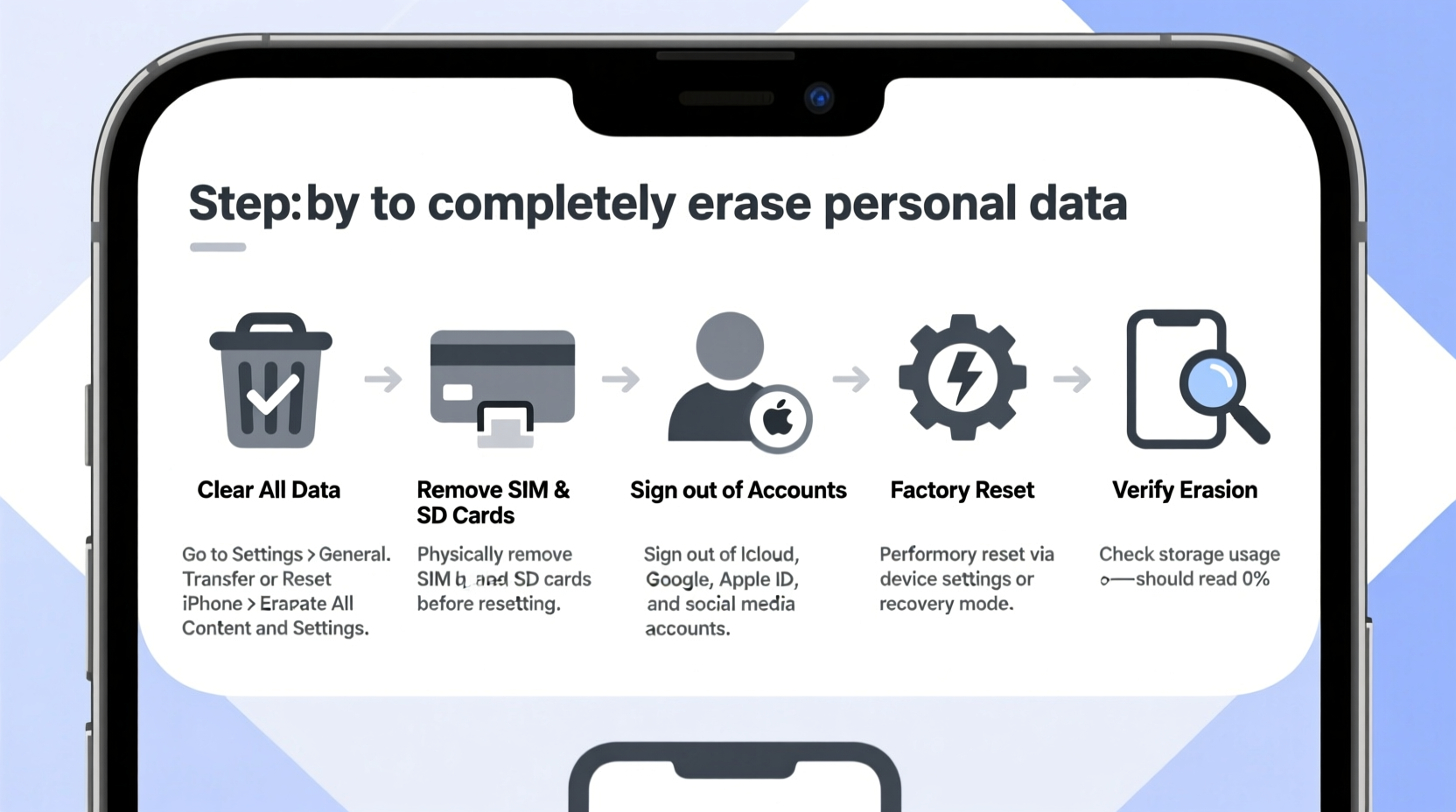
Step-by-Step Guide to Complete Data Erasure
To ensure your personal information is irrecoverable, follow this comprehensive sequence of actions tailored for both iOS and Android devices.
- Back Up Essential Data
Before beginning, back up any data you wish to keep—photos, contacts, documents—to a secure cloud service or encrypted external drive. - Remove SIM and SD Cards
These components often store contacts, messages, and media independently of internal storage. Physically remove them and either destroy, reuse, or securely wipe them separately. - Sign Out of All Accounts
On both iOS and Android, sign out of iCloud, Google, social media, email, and financial apps. This prevents remote access and disables activation locks. - Encrypt Your Device (Android Only – if not already enabled)
Go to Settings > Security > Encryption & credentials > Encrypt phone. This ensures all stored data is scrambled and tied to your passcode. - Perform a Full Factory Reset
- iOS: Settings > General > Transfer or Reset iPhone > Erase All Content and Settings.
- Android: Settings > System > Reset options > Erase all data (factory reset).
- Flood Internal Storage (Advanced Step)
After reset, refill the phone with dummy data—download large videos, fill the gallery with random images, record long audio clips—then perform another factory reset. This overwrites previously deleted data, making recovery nearly impossible.
Data Removal: iOS vs Android Comparison
| Feature | iOS (iPhone) | Android |
|---|---|---|
| Default Encryption | Yes (hardware-encrypted since iPhone 3GS) | Varies by model and OS version; most post-2017 devices support it |
| Activation Lock (Find My iPhone / Find My Device) | Disabled only after signing out first | Can be bypassed if not signed out manually |
| Residual Data Risk After Reset | Very low if signed out and reset properly | Moderate to high on older or unencrypted models |
| Recommended Overwrite Method | Not required due to secure enclave architecture | Fill storage with junk data pre- and post-reset |
| Time Required for Full Erasure | ~15–30 minutes | ~30–60+ minutes (longer with overwrite steps) |
Real-World Example: The Secondhand Phone Breach
In 2022, a cybersecurity researcher purchased five used Android phones from online marketplaces. Despite all showing “factory reset” status, he recovered full WhatsApp message histories, saved Wi-Fi passwords, login tokens for banking apps, and even a scanned copy of a driver’s license from one device. None of the previous owners had signed out of their Google accounts, and none had encrypted their phones prior to sale.
This case illustrates how easily overlooked steps can lead to serious privacy exposure. One phone, originally owned by a financial advisor, contained client contact lists and calendar entries with meeting notes—data that could have been exploited for phishing or social engineering attacks.
Essential Checklist Before Selling or Recycling
- ✅ Backed up important files to a secure location
- ✅ Removed SIM and microSD cards
- ✅ Signed out of iCloud, Google, Microsoft, and social media accounts
- ✅ Disabled Find My iPhone / Find My Device
- ✅ Encrypted the device (Android, if applicable)
- ✅ Performed factory reset
- ✅ Filled storage with dummy data and reset again (recommended for Android)
- ✅ Verified no personal data remains by turning the phone back on
Frequently Asked Questions
Can someone really recover my data after a factory reset?
Yes, especially on Android devices without full-disk encryption. Data recovery tools can scan raw memory for remnants of deleted files. iPhones are generally more secure due to hardware-level encryption and the Secure Enclave, provided the user signs out of iCloud first.
Is it safe to donate my phone after wiping it?
Only if you’ve followed all steps—including account sign-out and multiple overwrites for Android. Consider donating through certified e-waste recyclers who verify data destruction. Avoid giving phones to untrusted third parties without thorough sanitization.
Do I need special software to erase my phone?
Generally, no. Modern smartphones have built-in secure erase functions. However, for older Android devices, third-party tools like Dekhon or Blancco Mobile offer certified data wiping with verification reports—ideal for businesses or high-risk scenarios.
Final Steps and Peace of Mind
Erasing your phone isn’t just about freeing up space or preparing for a trade-in—it’s about protecting your identity and digital life. The few extra minutes spent ensuring complete data removal can prevent years of consequences from a single oversight.
Take control of your digital hygiene. Treat your smartphone like a personal vault: secure it while in use, and dismantle its contents completely when letting it go. By combining encryption, proper sign-out procedures, and data overwriting techniques, you can confidently release your device into the world, knowing your past stays private.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?