Your Apple ID is the key to your entire Apple ecosystem—from iCloud and the App Store to iMessage, FaceTime, and Find My. It holds personal data, payment methods, device access, and years of digital history. Yet, many users treat it as just another login without realizing how critical its security truly is. A compromised Apple ID can lead to data theft, unauthorized purchases, or even lock you out of your own devices. This guide walks you through every essential step to verify, strengthen, and manage your Apple ID with confidence.
Why Your Apple ID Security Matters
The Apple ID isn’t just a username—it’s a master key. With it, someone can reset passwords, track your location via Find My, restore device backups, make in-app purchases, and access emails, photos, and messages synced across devices. Apple has built-in protections like two-factor authentication and account recovery controls, but their effectiveness depends on how well you configure and maintain them.
According to Apple’s 2023 Security Transparency Report, over 78% of compromised accounts lacked two-factor authentication. That single setting dramatically reduces the risk of unauthorized access. Beyond that, regular verification of trusted devices, phone numbers, and recovery options ensures you stay in control—even if your information changes or your devices are lost.
“Your Apple ID is one of the most valuable digital identities you own. Treat it with the same care as your passport or bank account.” — Sarah Lin, Senior Security Analyst at Digital Trust Labs
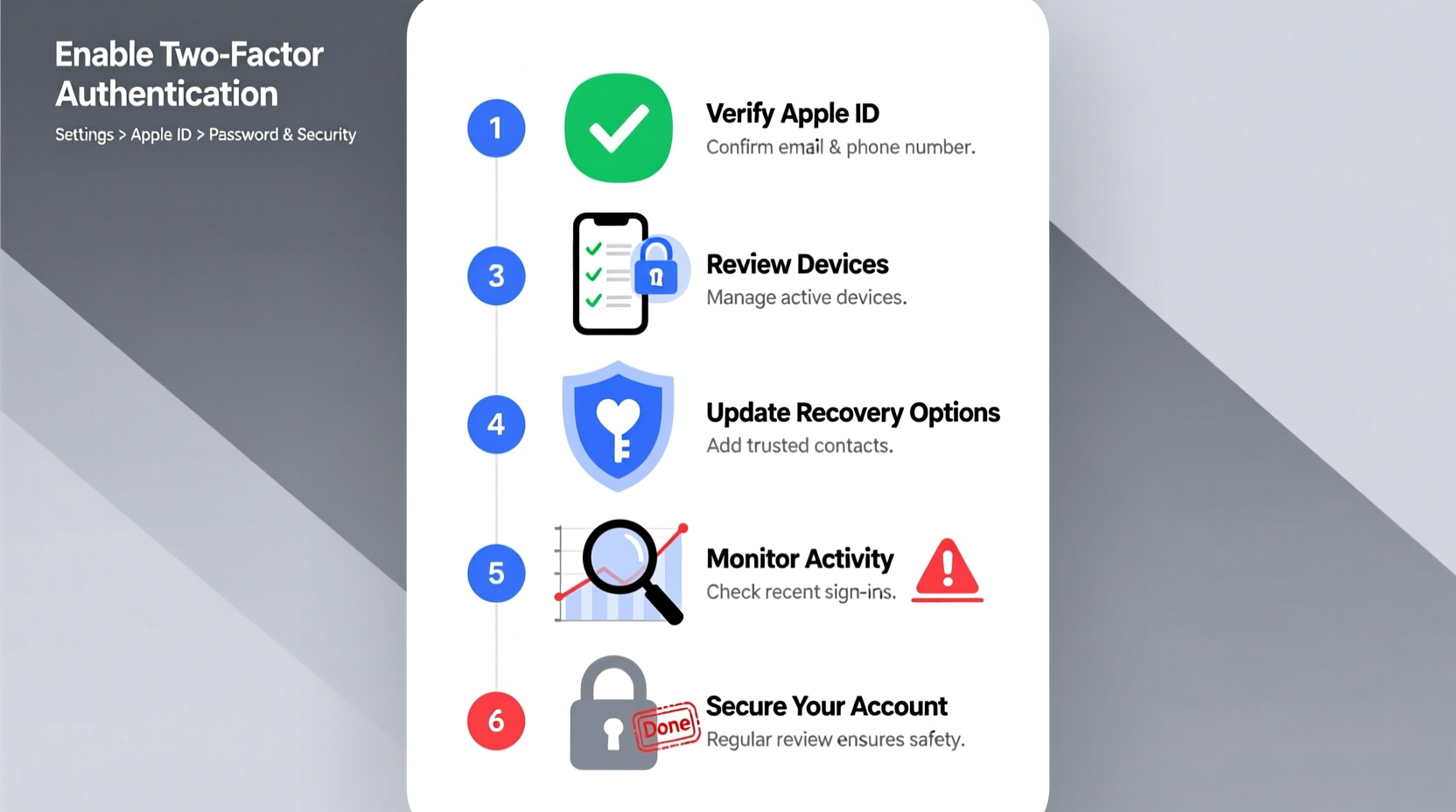
Step-by-Step: How to Verify Your Apple ID Settings
Start by confirming your current setup. Apple makes this easy through its centralized account management portal. Follow these steps to audit your Apple ID:
- Sign in to appleid.apple.com using your current credentials.
- Navigate to the Security section and review:
- Two-Factor Authentication status
- Trusted phone numbers
- Recovery key (if enabled)
- Account Recovery Contacts
- Under Devices, check all active devices linked to your account. Remove any you no longer use or don’t recognize.
- In Reachable At, confirm your primary email and rescue email are up to date.
- Review Payment Methods and remove outdated cards.
Essential Security Features You Should Enable
Apple offers layered protection tools. Here's what you must enable—and why:
Two-Factor Authentication (2FA)
This is non-negotiable. Once enabled, signing in on a new device requires both your password and a six-digit verification code sent to a trusted device or phone number. Even if someone steals your password, they can’t log in without physical access to your device.
Account Recovery Contacts
If you ever lose access to your password and trusted devices, Apple allows you to designate up to five trusted contacts who can help you regain entry. These people receive a special recovery code and must assist you in unlocking your account. Choose individuals you trust implicitly and inform them in advance.
Recovery Key (Advanced Users)
For maximum control, generate a recovery key—a 28-character code that acts as a backup to unlock your account if all other methods fail. Store it offline in a secure place like a safe or password manager. Warning: losing this key with no recovery contacts means permanent lockout.
| Feature | Recommended? | Best For | Risks if Misconfigured |
|---|---|---|---|
| Two-Factor Authentication | ✅ Yes (Required) | All users | None—only enhances security |
| Account Recovery Contacts | ✅ Yes | Families, shared households | Contact may be unreachable when needed |
| Recovery Key | ⚠️ Optional (Experts Only) | Technically savvy users | Potential permanent account loss if misplaced |
Managing Trusted Devices and Phone Numbers
Trusted devices are those authorized to receive verification codes and approve sign-ins. Over time, old iPhones, iPads, or Macs may still appear in your list—even if you’ve sold or erased them. This creates a vulnerability.
To manage trusted devices:
- Go to appleid.apple.com → Devices
- Select each device and click “Remove” if it’s no longer yours.
- After removal, that device will no longer receive verification codes or appear in Find My.
Similarly, update your trusted phone number whenever you change carriers or deactivate a line. An outdated number prevents you from receiving 2FA codes during critical moments like password resets.
Real Example: Recovering a Compromised Account
Jamie, a freelance designer, noticed strange activity on her iPad: apps she didn’t download, iCloud photos missing, and a new device appearing in her account settings. She realized her Apple ID had been breached—likely due to a weak password reused across sites.
She took immediate action:
- Used her trusted iPhone to go to Settings > [her name] > Sign-In & Security.
- Changed her password immediately.
- Removed the unknown MacBook from her devices list.
- Verified her recovery contact was still valid.
- Enabled two-factor authentication (previously disabled).
Within 20 minutes, she regained full control. Because she acted quickly and had a trusted device, Apple prevented permanent damage. Jamie now uses a password manager and reviews her Apple ID monthly.
Checklist: Secure Your Apple ID in 10 Minutes
Use this checklist to ensure your Apple ID is locked down:
- ✅ Confirm two-factor authentication is ON
- ✅ Review and remove unrecognized devices
- ✅ Update your trusted phone number
- ✅ Verify your rescue email address
- ✅ Set up at least two account recovery contacts
- ✅ Remove expired or unused payment methods
- ✅ Generate and store a recovery key (optional but recommended)
- ✅ Audit app-specific passwords for third-party services
Frequently Asked Questions
What happens if I lose access to all my trusted devices?
You’ll need to use account recovery. If you’ve set up recovery contacts, they can help unlock your account. Without them, Apple will verify your identity over time—this process can take up to two weeks and requires submitting official ID.
Can I disable two-factor authentication once it’s turned on?
No. Once enabled, two-factor authentication cannot be disabled for security reasons. This prevents attackers from weakening your account after gaining partial access.
Is it safe to use my Apple ID on third-party apps?
Yes, but use “Sign in with Apple” when available. It hides your real email and generates unique, random addresses for each service, reducing tracking and spam. Avoid sharing your Apple ID password directly with any app.
Final Thoughts: Make Security Routine, Not Reactive
Most people only think about Apple ID security after something goes wrong. But true protection comes from proactive habits. Set a calendar reminder every 90 days to review your Apple ID settings. Ensure your recovery options are current, trusted devices are accurate, and your password remains strong.
Remember, Apple provides powerful tools—but you’re the final layer of defense. By taking just ten minutes now, you safeguard years of memories, communications, and digital work. Don’t wait for a breach to act.









 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4
Comments
No comments yet. Why don't you start the discussion?