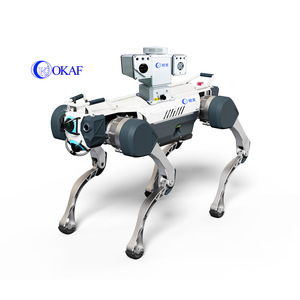
Artificial Intelligence And Security





 1/3
1/3






 1/3
1/3

 CN
CN









 1/3
1/3





 1/3
1/3





 1/3
1/3





 1/3
1/3




 1/3
1/3





 1/3
1/3







 1/17
1/17




 1/3
1/3





 1/3
1/3








 1/28
1/28





 1/3
1/3





 1/3
1/3






 1/3
1/3




 0
0





 1/3
1/3






 1/3
1/3






 1/3
1/3
About artificial intelligence and security
Where to Find Artificial Intelligence and Security Suppliers?
The global artificial intelligence (AI) and security technology sector is highly decentralized, with innovation hubs concentrated in North America, Western Europe, and East Asia. The United States leads in AI algorithm development and cybersecurity software integration, hosting 45% of globally recognized AI research institutions and a mature ecosystem of enterprise-grade security solution providers. China contributes significantly to hardware deployment, particularly in smart surveillance systems, where Shenzhen’s electronics manufacturing clusters enable rapid prototyping and scale-up of AI-powered cameras and access control devices.
These regions benefit from deep integration between semiconductor suppliers, firmware developers, and cloud infrastructure operators. In Israel and Germany, specialized AI-security firms leverage government-backed R&D initiatives to advance threat detection algorithms and behavioral analytics, achieving compliance with stringent data protection frameworks such as GDPR and HIPAA. Buyers gain access to vertically aligned supply chains where edge computing devices are co-developed with on-premise or hybrid AI models, reducing latency and enhancing real-time response capabilities in physical and cyber-physical security applications.
How to Choose Artificial Intelligence and Security Suppliers?
Prioritize these verification protocols when selecting partners:
Technical Compliance
Require ISO/IEC 27001 certification for information security management systems. For deployments involving personal data, confirm GDPR, CCPA, or equivalent regulatory alignment. Cybersecurity solutions must demonstrate third-party penetration testing reports and adherence to NIST SP 800-53 or CIS Controls. Verify compatibility with existing IT infrastructure, including API support for SIEM integration and encryption standards (e.g., AES-256, TLS 1.3).
Production Capability Audits
Evaluate technical infrastructure and development maturity:
- Minimum 8 years of domain-specific experience in AI-driven security applications
- Dedicated machine learning engineering teams comprising ≥15% of technical staff
- In-house data labeling pipelines and model validation environments
Cross-reference product release cycles with customer-reported uptime metrics (target >99.5%) to assess software stability and update reliability.
Transaction Safeguards
Implement phased payment structures tied to milestone deliveries, especially for custom AI model training or system integration. Review contractual SLAs covering incident response times, vulnerability patching windows, and data sovereignty clauses. Pilot testing is critical—conduct 30-day proof-of-concept trials to benchmark false positive rates, facial recognition accuracy (measured against NIST FRVT benchmarks), and system interoperability before full deployment.
What Are the Best Artificial Intelligence and Security Suppliers?
| Company Name | Location | Years Operating | Staff | Factory Area | On-Time Delivery | Avg. Response | Ratings | Reorder Rate |
|---|---|---|---|---|---|---|---|---|
| Supplier data not available | ||||||||
Performance Analysis
Due to absence of specific supplier data, procurement decisions should rely on verified industry benchmarks and independent technology assessments. Historically, established vendors with long-term government or enterprise contracts demonstrate higher reorder rates, indicating strong post-deployment support and system adaptability. Prioritize suppliers offering transparent model governance frameworks, regular third-party audits, and documented retraining schedules for AI models to maintain performance integrity over time. For edge device sourcing, verify firmware update mechanisms and secure boot capabilities to mitigate supply chain compromise risks.
FAQs
How to verify artificial intelligence and security supplier reliability?
Validate certifications through official accreditation databases. Request redacted copies of security audit reports, including SOC 2 Type II or ISO 27001 surveillance certificates. Assess vendor transparency regarding data handling practices, model bias mitigation strategies, and adversarial attack resistance testing.
What is the average sampling timeline?
Software-based AI security modules typically undergo 2–4 week pilot deployment cycles. Hardware-integrated systems (e.g., AI-enabled CCTV) require 30–45 days for sample configuration, including firmware customization and network integration testing. Add 7–14 days for international shipping depending on destination.
Can suppliers ship AI and security solutions worldwide?
Yes, most suppliers support global delivery via cloud-based licensing or physical shipment. Confirm export compliance with local regulations—dual-use AI technologies may require authorization under Wassenaar Arrangement guidelines. For hardware exports, ensure IEC 62443 and CE marking compliance for EU markets.
Do manufacturers provide free samples?
Sample availability varies by product type. Cloud-based AI platforms often offer free trial licenses (14–30 days). Physical devices may incur sampling fees, typically recoverable upon order placement exceeding $10,000. Customized AI models usually require paid proof-of-concept engagements.
How to initiate customization requests?
Submit detailed use case requirements, including environment type (indoor/outdoor), supported protocols (ONVIF, RTSP, MQTT), and AI functionality scope (e.g., loitering detection, PPE compliance monitoring). Leading suppliers respond with architecture diagrams within 5 business days and deliver testable builds within 3–6 weeks.